Research Article
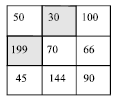
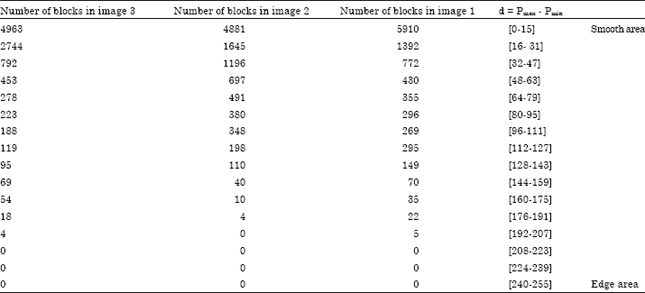
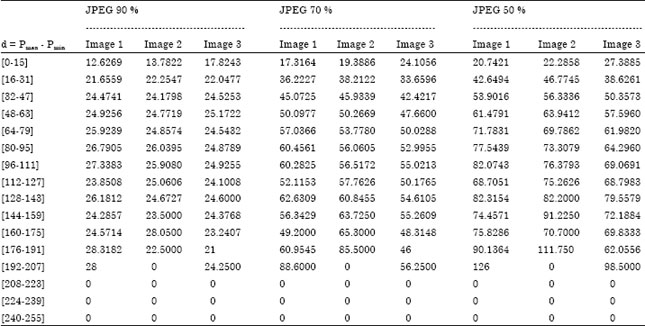
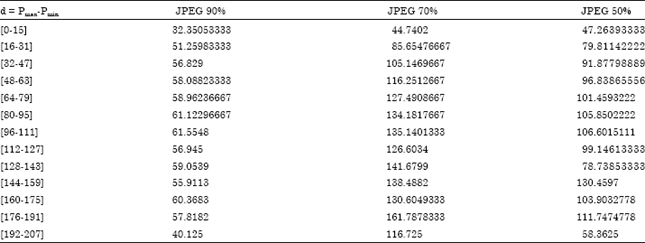
A Robust Watermark Embedding in Smooth Areas
Department of Information System, Kulliyyah of Information and Communication Technology, International Islamic University, Malaysia
Azizah A. Manaf
Advanced Informatics School, University Technology Malaysia, Malaysia
Adamu A. Ibrahim
Department of Information System, Kulliyyah of Information and Communication Technology, International Islamic University, Malaysia
Mazdak Zamani
Advanced Informatics School, University Technology Malaysia, Malaysia









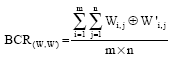
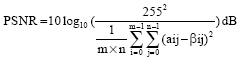
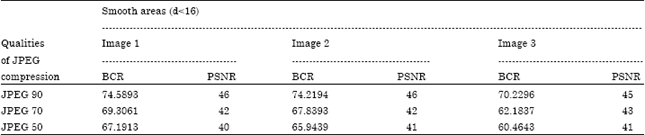
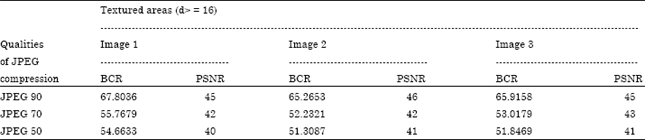
Johnson Reply
Extremely brilliant idea presented there