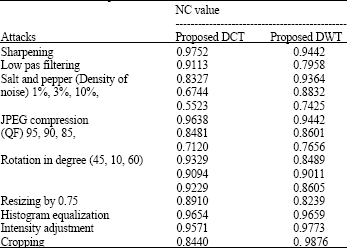
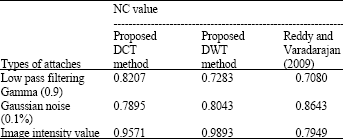
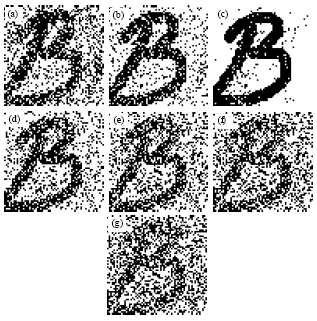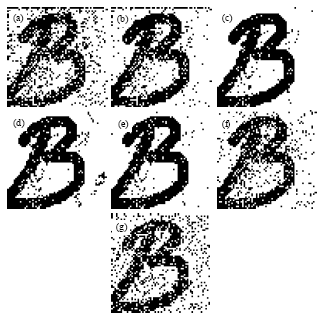Research Article
Robust Adaptive Image Watermarking using Visual Models in DWT and DCT Domain
School of computer and Communication, Hunan University, Changsha, 410082, China
Xingming Sun
School of computer and Communication, Hunan University, Changsha, 410082, China
Hengfu Yang
School of computer and Communication, Hunan University, Changsha, 410082, China
Nur Mohammad
School of computer and Communication, Hunan University, Changsha, 410082, China