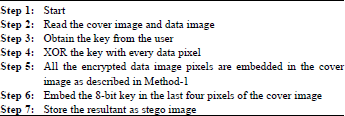
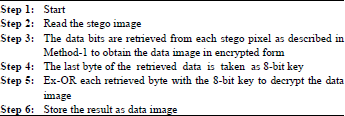
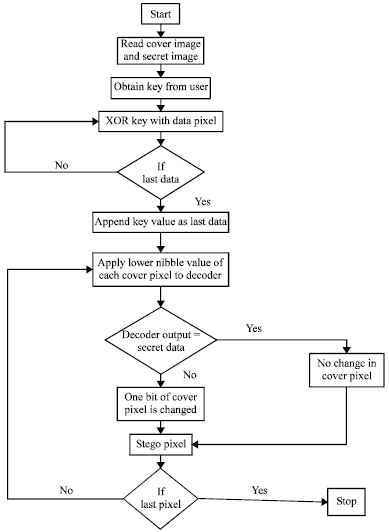
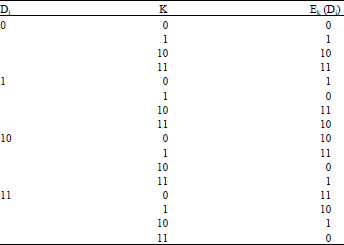Research Article
Cover as Key and Key as Data: An Inborn Stego
School of Electrical and Electronics Engineering, SASTRA University, 613401, India
Jagannathan Chakravarthy
School of Electrical and Electronics Engineering, SASTRA University, 613401, India
Badrinath Radhakrishnan
School of Electrical and Electronics Engineering, SASTRA University, 613401, India
K. Thenmozhi
School of Electrical and Electronics Engineering, SASTRA University, 613401, India
J.B.B. Rayappan
School of Electrical and Electronics Engineering, SASTRA University, 613401, India
Rengarajan Amirtharajan
School of Electrical and Electronics Engineering, SASTRA University, 613401, India