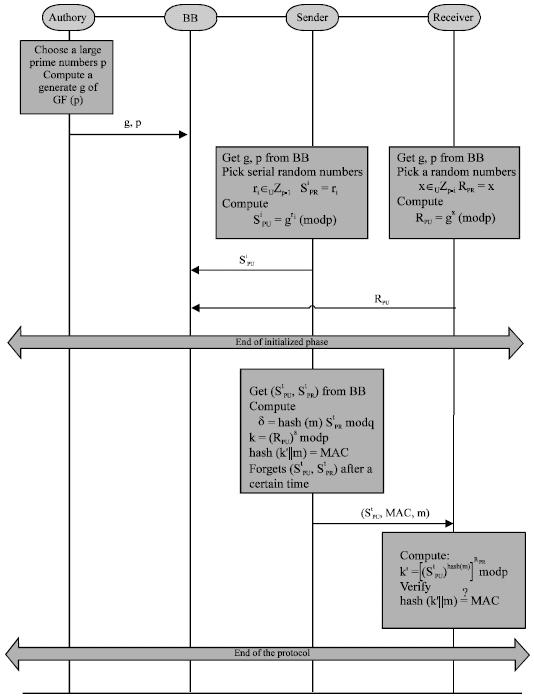
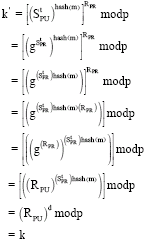
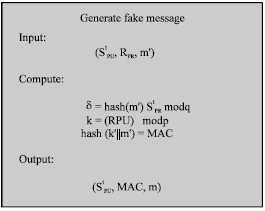
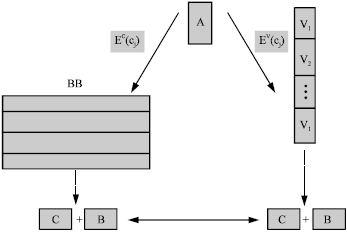
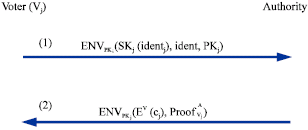
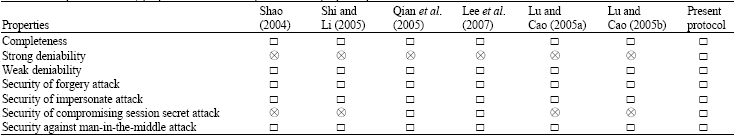
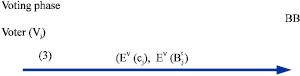Research Article
A Secure Non-Interactive Deniable Authentication Protocol with Strong Deniability Based on Discrete Logarithm Problem and its Application on Internet Voting Protocol
School of Computer, South-Center University for Nationalities, Wuhan, 430074, Hubei, People�s Republic of China