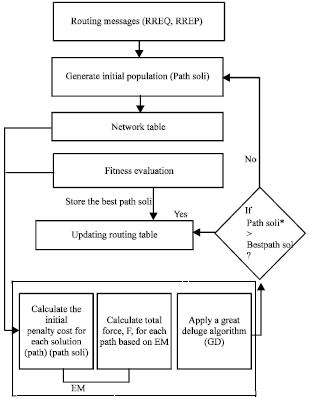
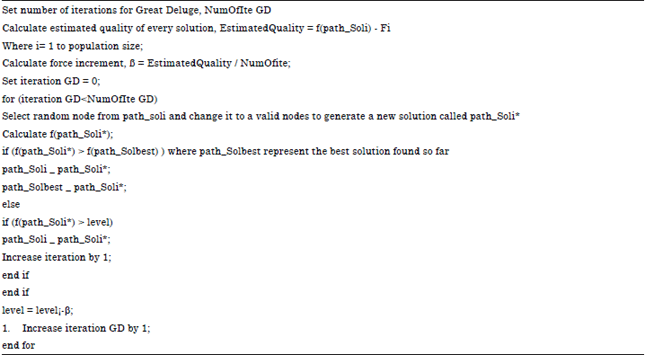
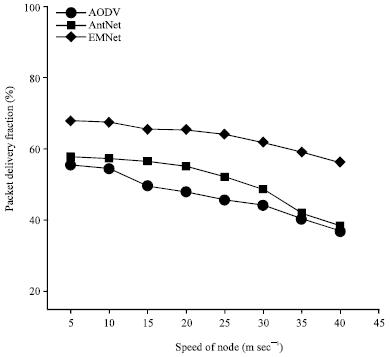
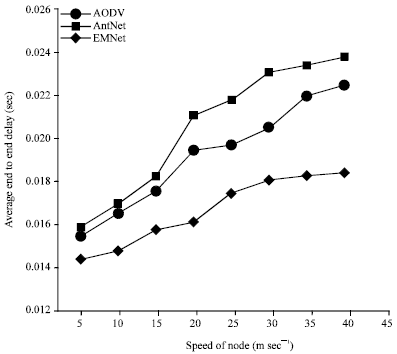
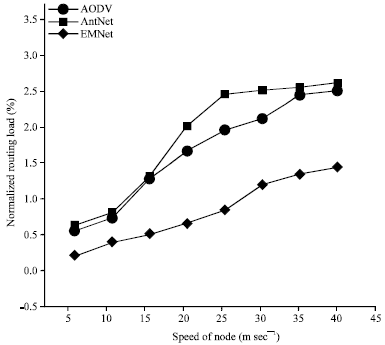
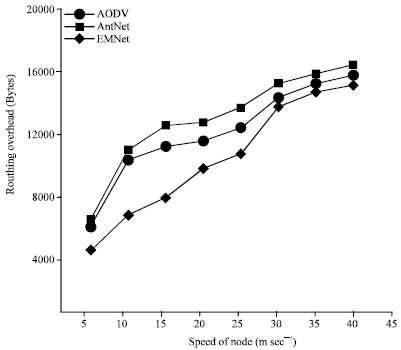
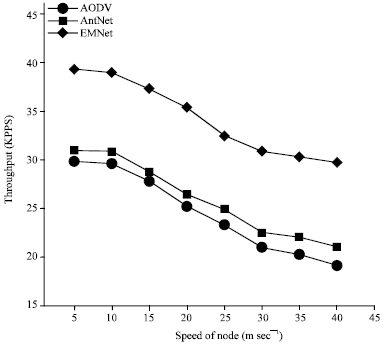
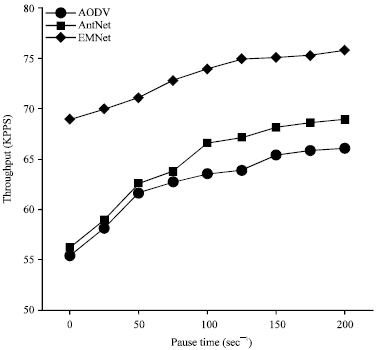
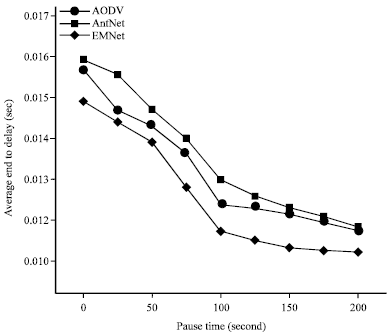
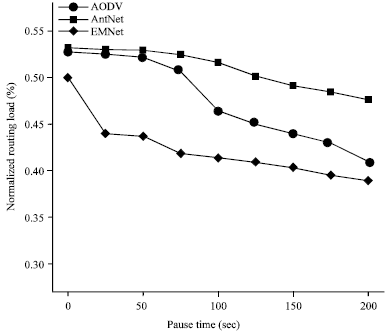
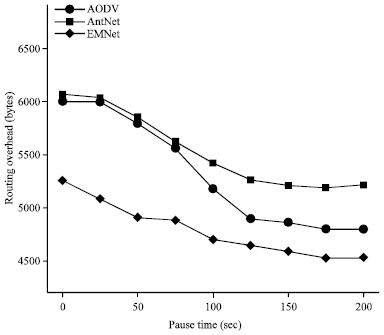
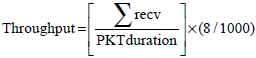Research Article
EMNet: Electromagnetic-like Mechanism based Routing Protocol for Mobile Ad Hoc Networks
Center of System and Machine Intelligence, Universiti Tenaga Nasional, 7 km, Jalan Ikram-Uniten,43000 Kajang, Selangor, Malaysia
H.Sh. Jassim
Center of System and Machine Intelligence, Universiti Tenaga Nasional, 7 km, Jalan Ikram-Uniten,43000 Kajang, Selangor, Malaysia
S. Yussof
College of Information Technology, Universiti Tenaga Nasional, 7 km, Jalan Ikram-Uniten,43000 Kajang, Selangor, Malaysia
S.P. Koh
Center of System and Machine Intelligence, Universiti Tenaga Nasional, 7 km, Jalan Ikram-Uniten,43000 Kajang, Selangor, Malaysia
David F.W. Yap
Faculty of Electronics and Computer Engineering, Universiti Teknikal Malaysia Melaka, Hang Tuah Jaya, 76109 Durian Tunggal, Melaka, Malaysia