Research Article
An Efficient Steganographic Method by using Image Fragments With High Security
School of Computing, SASTRA University, Thanjavur, Tamilnadu, India
S. Mohana
School of Computing, SASTRA University, Thanjavur, Tamilnadu, India
A steganographic system conceals secret data in a carrier image so as not to arouse a suspicion apart from the sender and receiver. According to Stefan and Fabin (2000), Steganography is secret way of communicating by hiding the existence of communication itself. Cryptograohy is the well known cousin of steganography where the message is scrambled to prevent the message from hackers (Salem et al., 2011; Amirtharajan et al., 2011, 2012).
In the present digital world, a steganographic system keeps the presence of secret data imperceptible (Amirtharajan and Rayappan, 2012a-d; Cheddad et al., 2010; Janakiraman et al., 2012a, b). But steganographic system tends to be detectable in the cover medium. Even if secret data is not detected, the existence of it modifies the carrier image’s statistical properties. This leads to eavesdroppers to easily identify the changes in the properties of Stegoimage (Amirtharajan et al., 2012).
This study introduces a new steganographic system of hiding the secret data with higher anti-steganalysis capability by adding the fragmented data files of secret image as layers to the carrier image.
RELATED WORK
In steganography, embedding the secret bits in the redundant bits of the stego object and transmits as a carrier image (Karthikeyan et al., 2012; Padmaa et al., 2011; Rajagopalan et al., 2012; Thanikaiselvan et al., 2011; Thenmozhi et al., 2012). Presently, most of the steganographic processes depend on the size of the carrier image. Thus a large sized secret data cannot be embedded in a carrier image of smaller size. Moreover there are chances for the carrier image to overflow when certain crypto algorithms are used during encryption. In such cases, a part of the secret image will be lost.
Considering these as the barriers in steganographic system this proposed model overcomes these difficulties.
PROPOSED WORK
As told earlier this idea mainly focuses on undetectability. So this framework begins by splitting the secret image into two segments of odd and even bytes. These are embedded into the carrier image in layers sequentially along with the encrypted text. This forms the Stegoimage. This is sent to the receiver. The receiver first isolates the carrier image and the hidden data (two segments of hidden image and encrypted text). Then the receiver uses the pass-key and retrieves the original hidden image and plain text from the encrypted text. The detailed implementation of this idea is as follows.
HIDING PROCESS
The sender first loads the secret image. This image is divided into two segments. The first segment consists of all the odd bytes and the second segment consists of all the even bytes. These are stored as separate data files. Then the binary data of the carrier image that is selected is followed by the sentinel string which is used to distinguish the carrier image from the rest of the layers. Then the above two data files are embedded sequentially with pass-key as the delimiter between them. This pass-key is also used to encrypt the text using Data Encryption Standard. This encrypted text is also embedded into the carrier image. Thus the Stegoimage consists of carrier image followed by a sentinel string which separates the carrier image from rest of the layers. This sentinel string is followed by the odd bytes data file, the even bytes data file and the encrypted text being embedded sequentially in layers with pass-key as the delimiter. This Stegoimage is sent to the receiver. The implementation of hiding process is presented in the form of an algorithm as follows.
Hiding algorithm: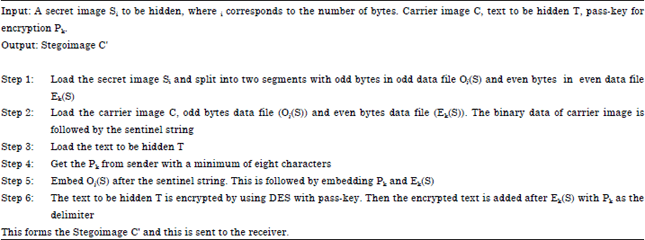 |
RETRIEVING PROCESS
The receiver loads the Stegoimage after which the receiver isolates the carrier image and the hidden data (secret image and encrypted text) with sentinel string as the delimiter. From this hidden data the receiver extracts the (1) odd bytes data (2) even bytes data (3) encrypted text separately by using pass-key as the delimiter. The retrieving process is carried out only if the receiver’s pass-key matches with the pass-key in the Stegoimage. Then the hidden image is formed by merging the odd byte file and even byte file alternatively. Finally the encrypted text is decrypted by using Data Encryption Standard algorithm with pass-key.
Retrieving algorithm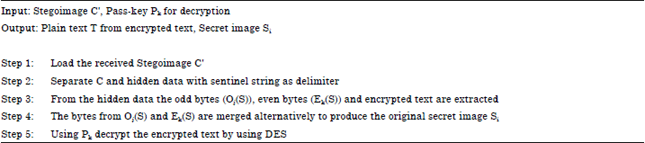 |
ALGORITHM IMPLEMENTATION
As an implementation of the hiding process, Fig. 1 acts as the secret image which is segmented into two data files (Oj(S)-odd bytes and Ek (S)-even bytes). Figure 2 acts as the carrier image (C) which will be loaded with two data files Oj (S) and Ek (S) and the encrypted form of text to be hidden using pass-key. This process produce the StegoImage C'.
In Fig. 3, the process of hiding secret image and the text with Carrier Image is shown.
The retrieving process loads the Stegoimage C' and checks the pass-key with the hidden data, if it matches, it extracts the secret image (Si) and the decrypted text.
In Fig. 4 the process of extracting the secret image (Fig. 5) and the hidden text with the use of correct pass-key (Pk) is shown.
 | |
| Fig. 1: | Sample secret image (Si) to be segmented into two data files |
 | |
| Fig. 2: | Sample carrier image (C) which will be loaded with two data files |
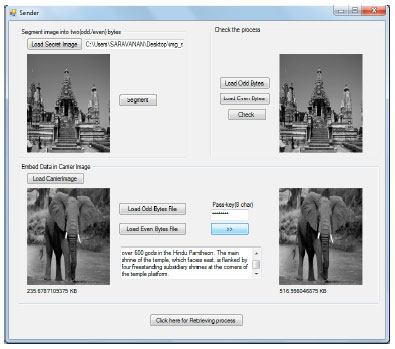 | |
| Fig. 3: | Hiding secret image and Text in a carrier image |
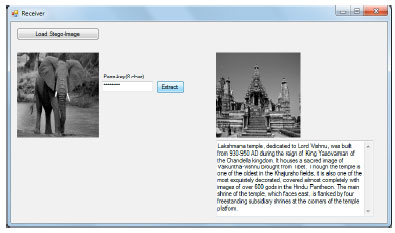 | |
| Fig. 4: | Retrieving secret image and text from carrier image |
 | |
| Fig. 5: | Retrieved secret image from the carrier image |
This study introduces a new steganographic system of hiding the secret data with high security. This is ensured by dividing the secret image into two segments. Moreover, this method does not depend on the size of carrier image. Thus a secret data of any size can be embedded into the carrier image in layers without affecting the statistical properties of carrier image. This method can be further extended to hide multimedia data.