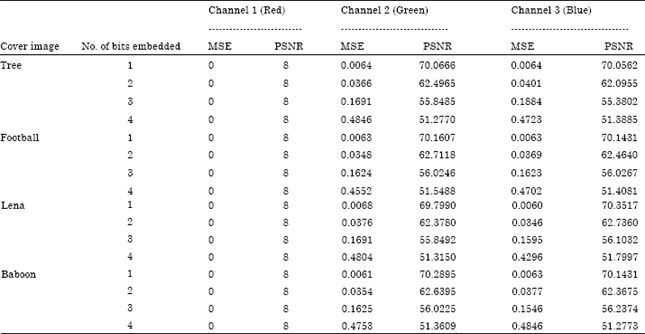
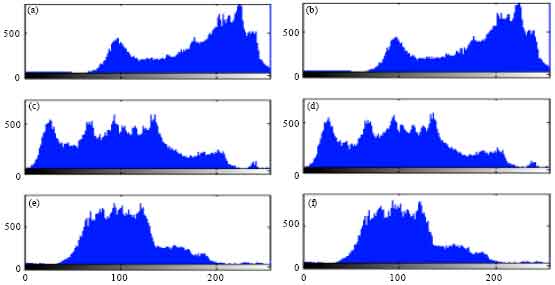
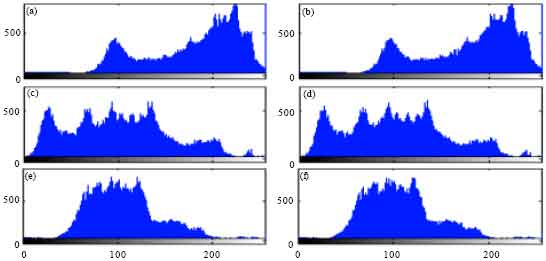
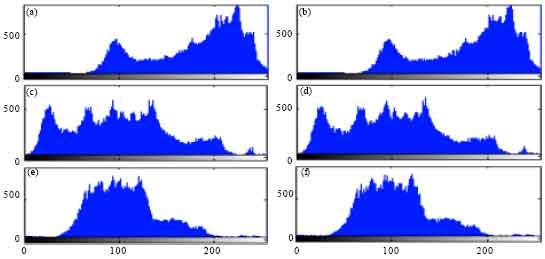
Research Article
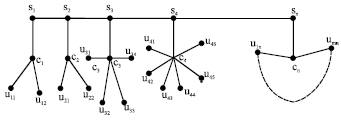
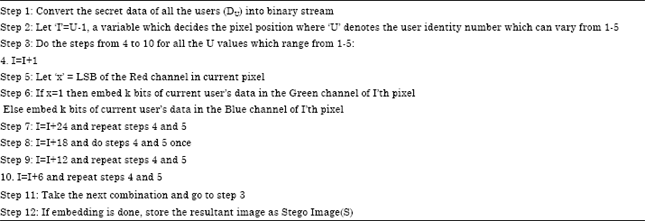
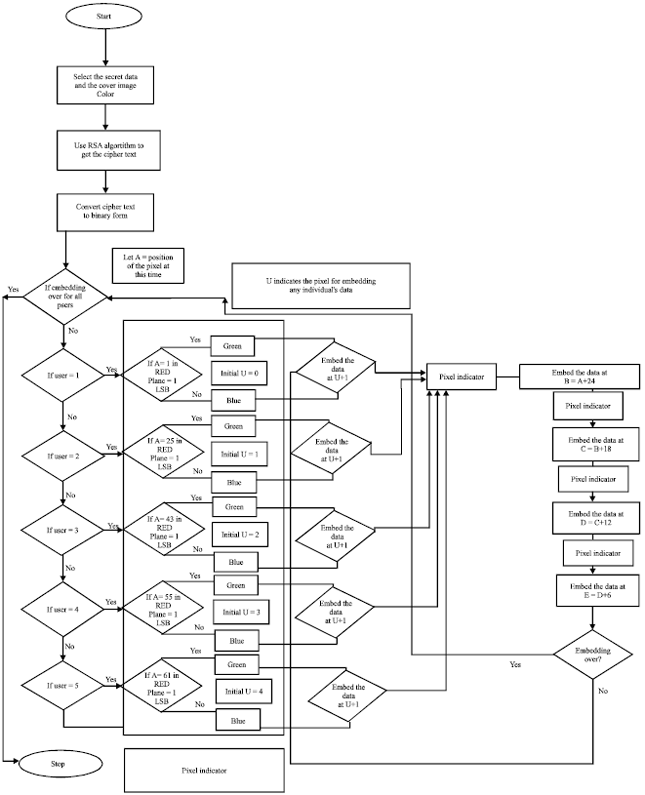
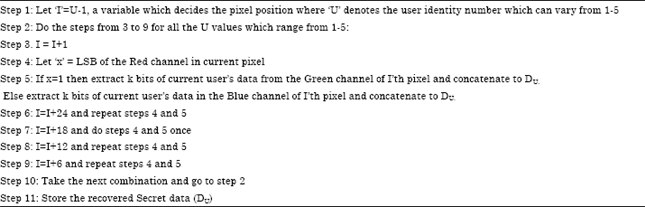
Graceful Labeling of Assignable Information Hiding in Image
School of Humanities and Sciences, SASTRA University Thanjavur, Tamil Nadu, India
T.N. Janakiraman
NIT, Trichy, SASTRA University Thanjavur, Tamil Nadu, India
N. Sairam
School of Computing, SASTRA University Thanjavur, Tamil Nadu, India
N.R. Raajan
School of Electrical and Electronics Engineering, SASTRA University Thanjavur, Tamil Nadu, India
K.S. Mathavan
School of Electrical and Electronics Engineering, SASTRA University Thanjavur, Tamil Nadu, India
P. Praveenkumar
School of Electrical and Electronics Engineering, SASTRA University Thanjavur, Tamil Nadu, India
R. Krishnakumar
School of Electrical and Electronics Engineering, SASTRA University Thanjavur, Tamil Nadu, India
M. Malligaraj
School of Electrical and Electronics Engineering, SASTRA University Thanjavur, Tamil Nadu, India
K. Karthikeyan
School of Electrical and Electronics Engineering, SASTRA University Thanjavur, Tamil Nadu, India