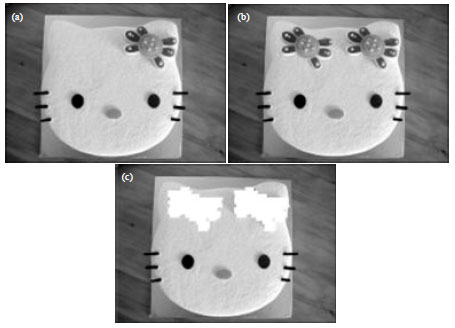
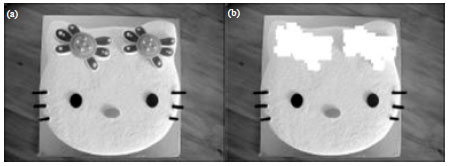
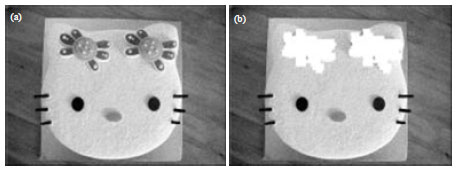
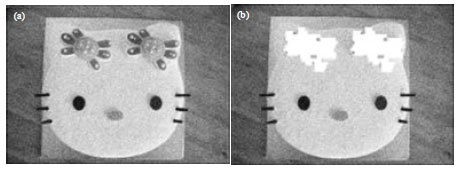
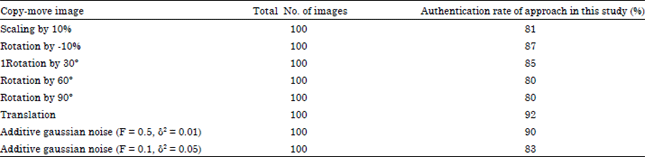
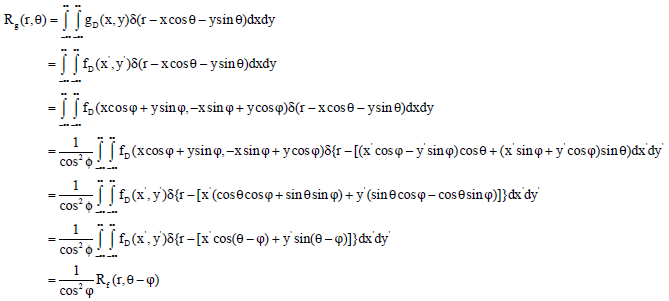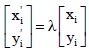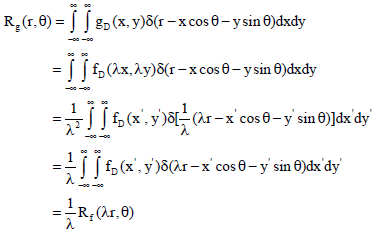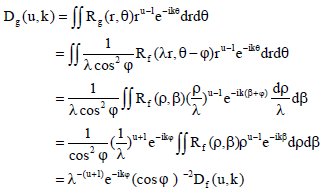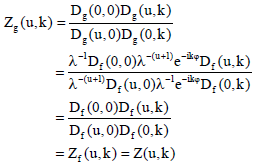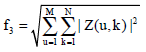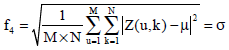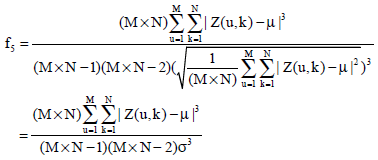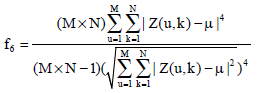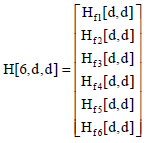Research Article
A Copy-Move Forgery Image Blind Authentication Approach Based on Radon-Pseudo-Fourier-Mellin-Transform
School of Information Engineering, Guangdong Mechanical and Electrical College, Guangdong University of Foreign Studies South China Business College, Guangzhou, 510545, China
Yanfen Gan
Department of Information Science and Technology, Guangdong University of Foreign Studies South China Business College, Guangzhou, 510545, China