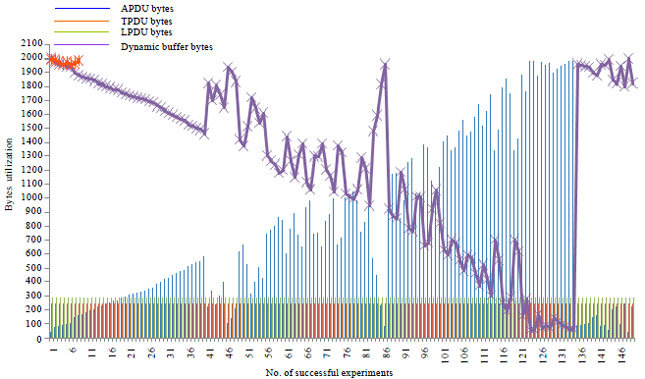
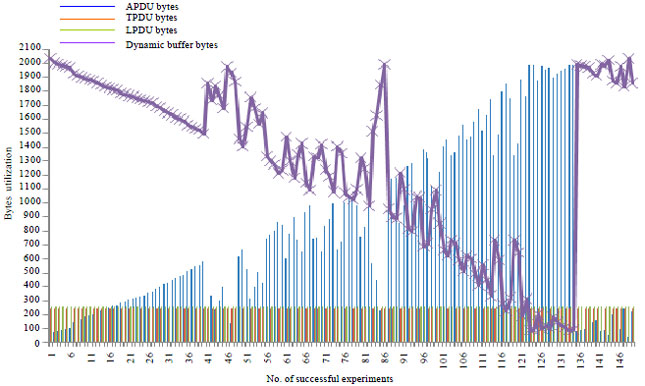
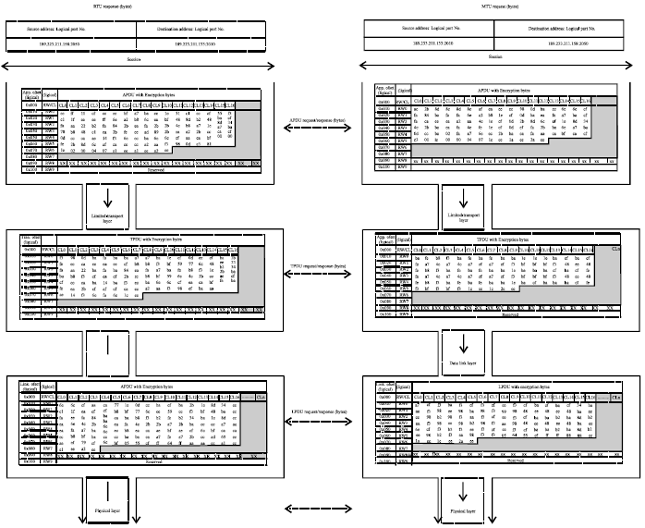
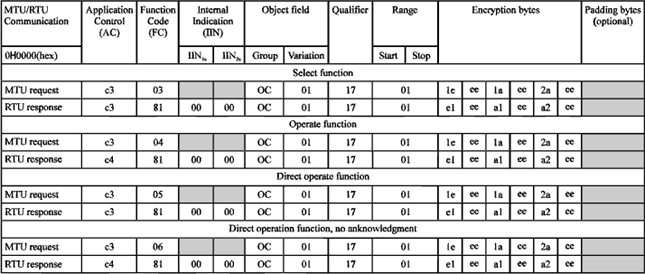
Research Article
Deployment of New Dynamic Cryptography Buffer for SCADA Security Enhancement
Malaysian Institute of Information Technology (MIIT), 1016,Jalan Sultan Ismail, Universiti Kuala Lumpur, 50250, Kuala Lumpur, Malaysia
S. Musa
Malaysian Institute of Information Technology (MIIT), 1016,Jalan Sultan Ismail, Universiti Kuala Lumpur, 50250, Kuala Lumpur, Malaysia
M. Irfan
Windfield College, Paser Seni, Kuala Lumpur, Malaysia
S. Asadullah
Kulliyah of Information and Communication Technology, International Islamic University, Malaysia