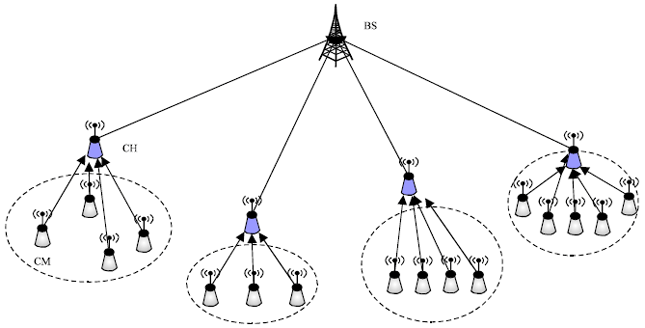
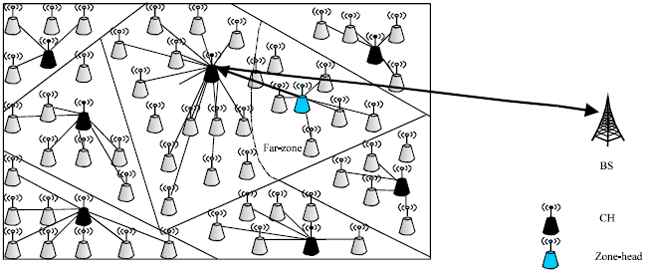
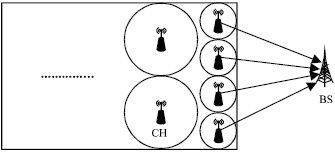
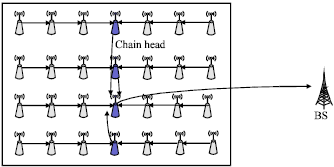
Review Article
A Survey on Cluster-based Routing Protocols in Wireless Sensor Networks
Department of Communication Technology and Network, Faculty of Computer Science and Information Technology, Universiti Putra Malaysia, Serdang,43400, Selangor, Malaysia
Zurina Mohd Hanapi
Department of Communication Technology and Network, Faculty of Computer Science and Information Technology, Universiti Putra Malaysia, Serdang,43400, Selangor, Malaysia