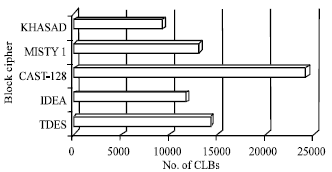
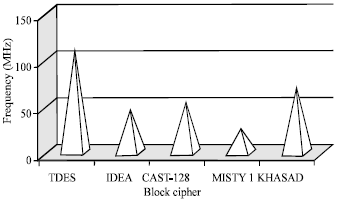
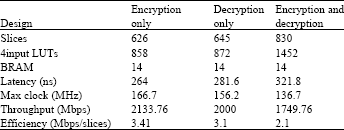
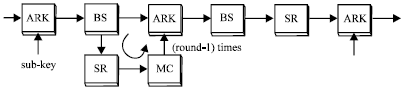
Review Article
Survey and Analysis of Hardware Cryptographic and Steganographic Systems on FPGA
Faculty, School of Electrical and Electronics Engineering, SASTRA University, Tirumalaisamudram, Thanjavur-613401, India
Rengarajan Amirtharajan
Faculty, School of Electrical and Electronics Engineering, SASTRA University, Tirumalaisamudram, Thanjavur-613401, India
Har Narayan Upadhyay
Faculty, School of Electrical and Electronics Engineering, SASTRA University, Tirumalaisamudram, Thanjavur-613401, India
John Bosco Balaguru Rayappan
Faculty, School of Electrical and Electronics Engineering, SASTRA University, Tirumalaisamudram, Thanjavur-613401, India