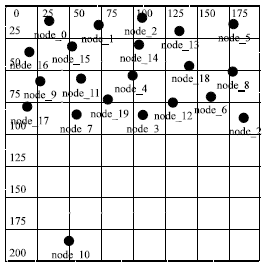
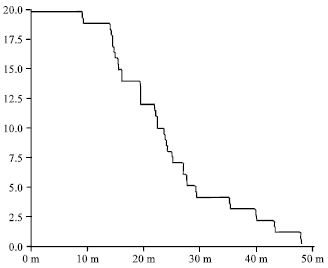
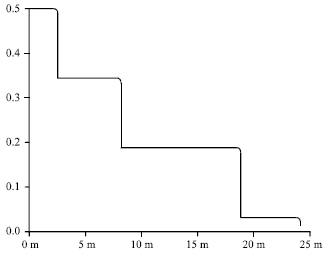
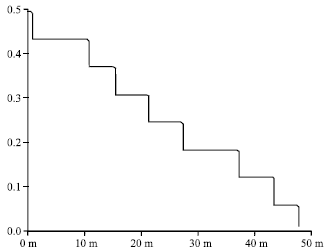
Research Article
Study on an Improved Algorithm based on LEACH Protocol
School of Natural Sciences, Nanjing University of Posts and Telecommunications, Nanjing, 210003, China
Wei Wei
School of Computer Science and Engineering, Xi�an University of Technology, Xi�an 710048, China
Ang Wei
School of Natural Sciences, Nanjing University of Posts and Telecommunications, Nanjing, 210003, China