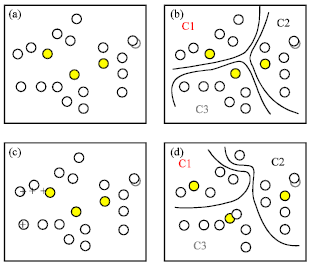
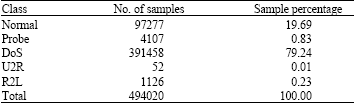
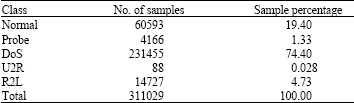
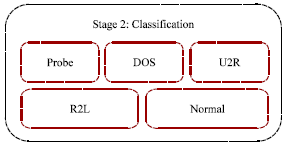
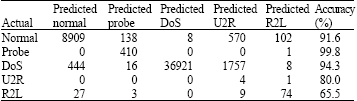
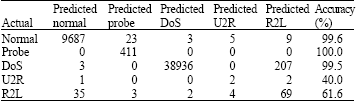
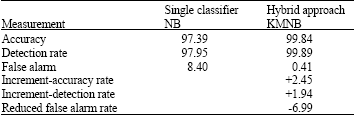
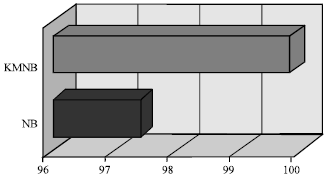
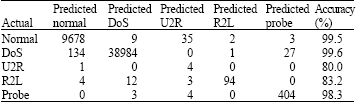
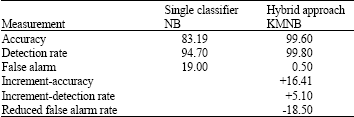
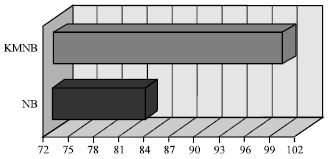
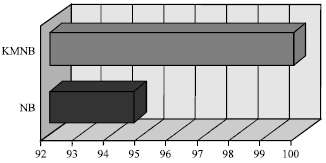
Research Article
A K-Means and Naive Bayes Learning Approach for Better Intrusion Detection
Faculty of Computer Science and Information Technology, University Putra Malaysia, 43400 UPM Serdang, Selangor, Darul Ehsan, Malaysia
W. Yassin
Faculty of Computer Science and Information Technology, University Putra Malaysia, 43400 UPM Serdang, Selangor, Darul Ehsan, Malaysia
M. N. Sulaiman
Faculty of Computer Science and Information Technology, University Putra Malaysia, 43400 UPM Serdang, Selangor, Darul Ehsan, Malaysia
N. I. Udzir
Faculty of Computer Science and Information Technology, University Putra Malaysia, 43400 UPM Serdang, Selangor, Darul Ehsan, Malaysia