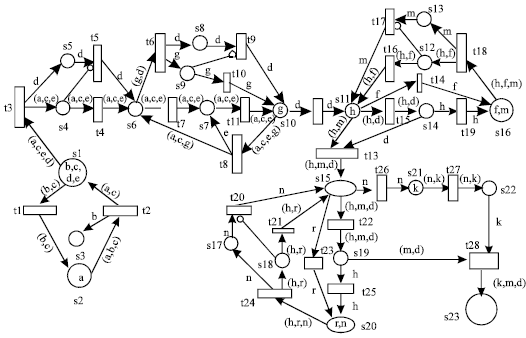
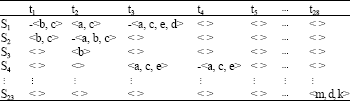
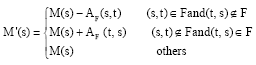Research Article
Security Infrastructure Verification of Library Information Grid Based on ePr/T net
Department of Information and Computing Science, Anhui University of Science and Technology, Huainan Anhui, 232001, China
Xiao-Qin Fan
School of Computer and Information Technology, Shanxi University, Taiyuan Shanxi, 030006, China
Yan-Ni Zou
Department of Information and Computing Science, Anhui University of Science and Technology, Huainan Anhui, 232001, China