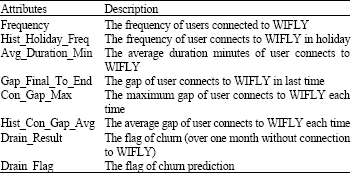
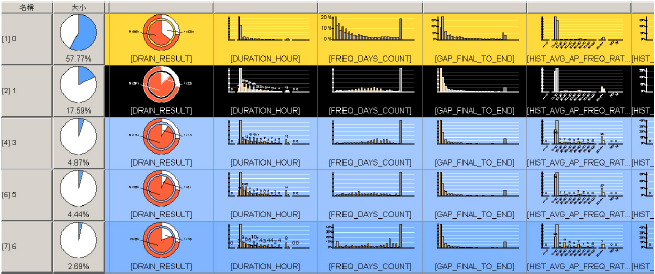
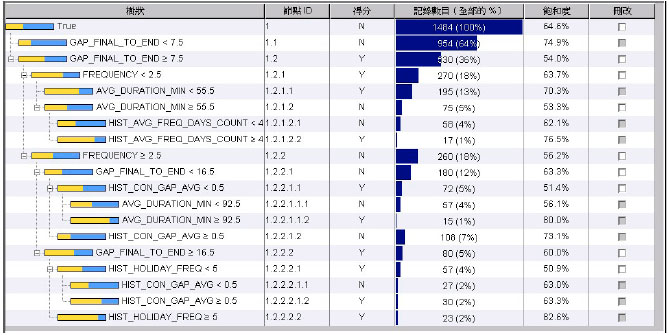
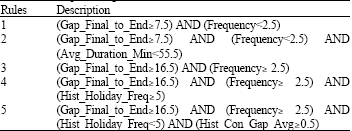
Research Article
Applying Data Mining Techniques to WIFLY in Customer Relationship Management
Department of Information Management, Chang Gung Institute of Technology, Kwei-Shan, Taoyuan County 333, Taiwan, Republic of China
Ding-An Chiang
Department of Computer Science and Information Engineering, Tamkang University, Tamsui, Taipei County 251, Taiwan, Republic of China
Sheng-Wei Lai
Communication Development Office, Ministry of National Defense, Shindian, Taipei County 231, Taiwan, Republic of China
Cheng-Jung Lin
Department of Computer Science and Information Engineering, Tamkang University, Tamsui, Taipei County 251, Taiwan, Republic of China