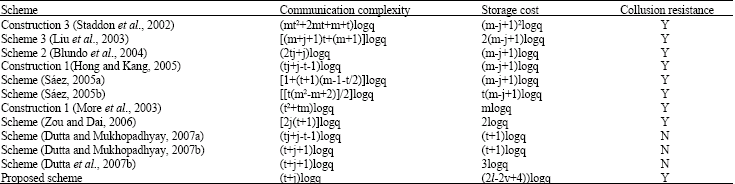
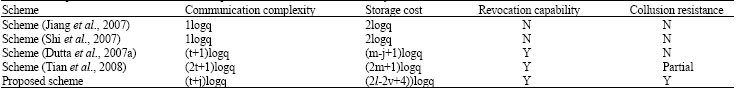
Short Communication
Anti-collusive Self-healing Key Distribution Scheme with Revocation Capability
Research Center of Computer Network and Information Security Technology, Harbin Institute of Technology, Harbin, 150001, People`s Republic of China
MingZeng Hu
Research Center of Computer Network and Information Security Technology, Harbin Institute of Technology, Harbin, 150001, People`s Republic of China
HongLi Zhang
Research Center of Computer Network and Information Security Technology, Harbin Institute of Technology, Harbin, 150001, People`s Republic of China
WeiZhe Zhang
Research Center of Computer Network and Information Security Technology, Harbin Institute of Technology, Harbin, 150001, People`s Republic of China