Research Article
Rubik’s Cube Blend with Logistic Map on RGB: A Way for Image Encryption
School of Electrical and Electronics Engineering, SASTRA University, Thanjavur, Tamil Nadu, India
G. Ashwin
School of Electrical and Electronics Engineering, SASTRA University, Thanjavur, Tamil Nadu, India
S.P. Kartavya Agarwal
School of Electrical and Electronics Engineering, SASTRA University, Thanjavur, Tamil Nadu, India
S. Naveen Bharathi
School of Electrical and Electronics Engineering, SASTRA University, Thanjavur, Tamil Nadu, India
V. Suraj Venkatachalam
School of Electrical and Electronics Engineering, SASTRA University, Thanjavur, Tamil Nadu, India
K. Thenmozhi
School of Electrical and Electronics Engineering, SASTRA University, Thanjavur, Tamil Nadu, India
Rengarajan Amirtharajan
School of Electrical and Electronics Engineering, SASTRA University, Thanjavur, Tamil Nadu, India









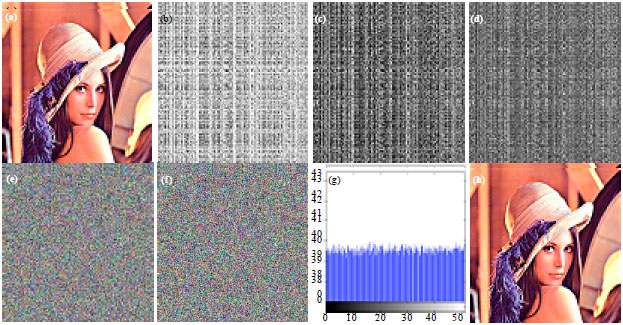
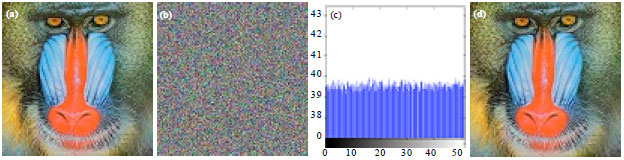
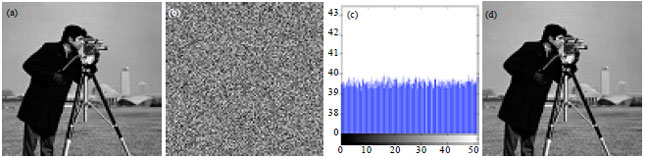
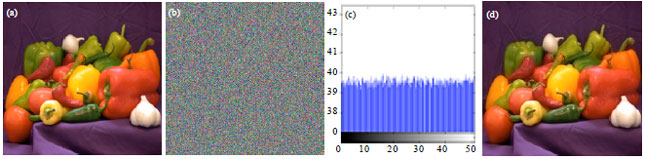
Hayat Ali Reply
can you help me please .. I want the Rubik program that you used in this article because I need it.
please help me