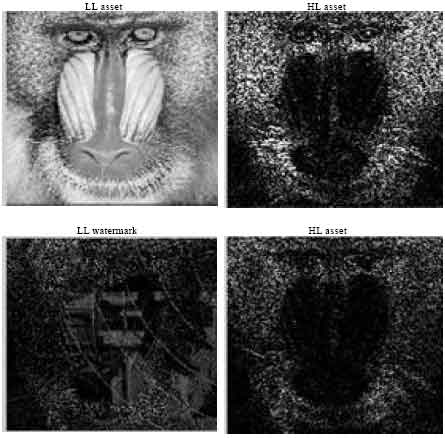
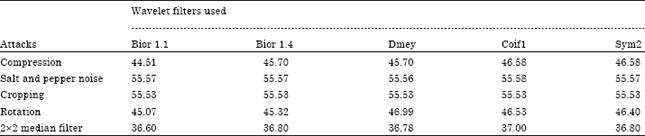
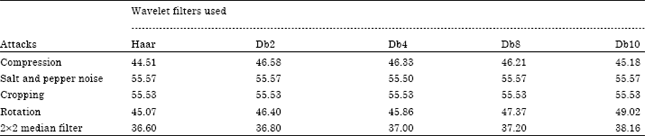
Research Article
Comparison of Wavelet Filters in Hybrid Domain Watermarking
Department of Electronics and Communication Engineering, SASTRA University, India
K. Narasimhan
Department of Electronics and Communication Engineering, SASTRA University, India
P.V.M. Vijayabhaskar
Department of Electronics and Communication Engineering, SASTRA University, India
G. Shiva
Department of Electronics and Communication Engineering, SASTRA University, India