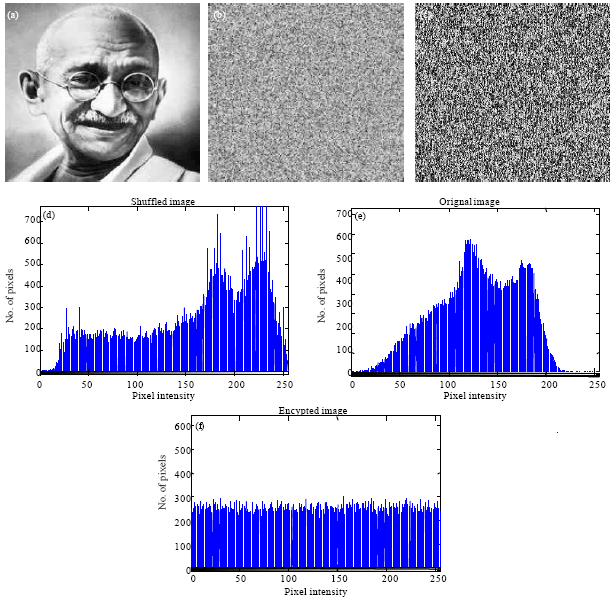
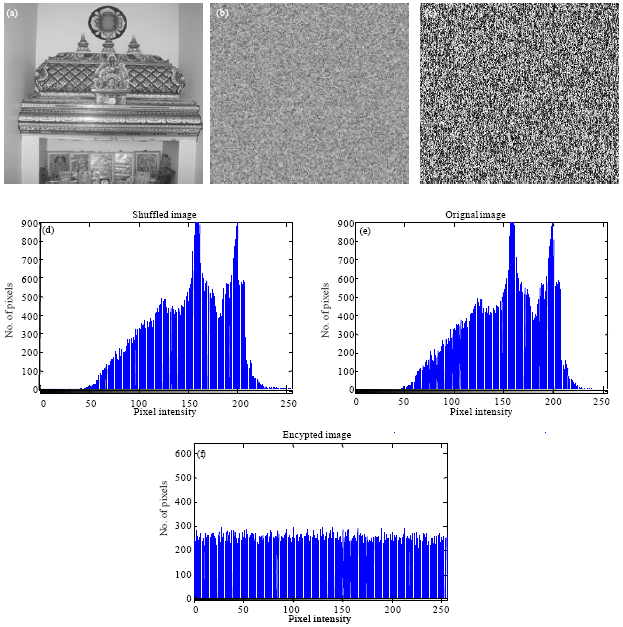
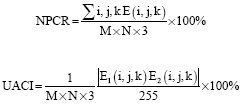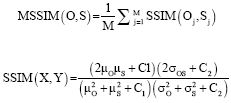Research Article
Why Image Encryption for Better Steganography
School of Electrical and Electronics Engineering, SASTRA University, India
P. Archana
School of Electrical and Electronics Engineering, SASTRA University, India
J.B.B. Rayappan
School of Electrical and Electronics Engineering, SASTRA University, India