Research Article
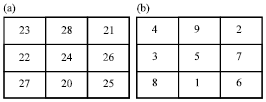
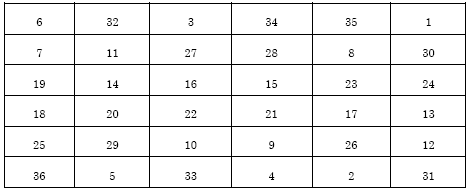
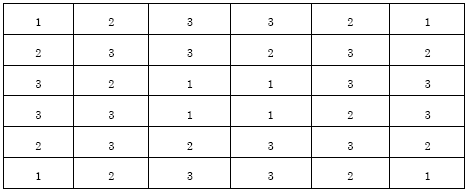
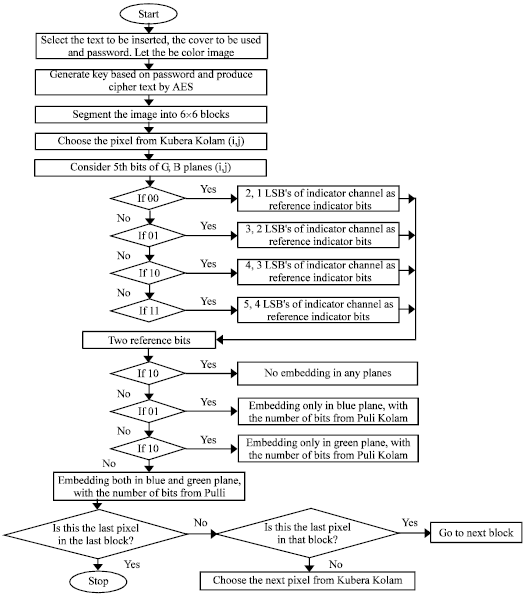
Kubera Kolam: A Way for Random Image Steganography
Department of Electronics and Communication Engineering, School of Electrical and Electronics Engineering, SASTRA University, Thanjavur, 613 401, India
Krishnamourthy Karthikeyan
Department of Electronics and Communication Engineering, School of Electrical and Electronics Engineering, SASTRA University, Thanjavur, 613 401, India
Malligaraj Malleswaran
Department of Electronics and Communication Engineering, School of Electrical and Electronics Engineering, SASTRA University, Thanjavur, 613 401, India
J.B.B. Rayappan
Department of Electronics and Communication Engineering, School of Electrical and Electronics Engineering, SASTRA University, Thanjavur, 613 401, India

















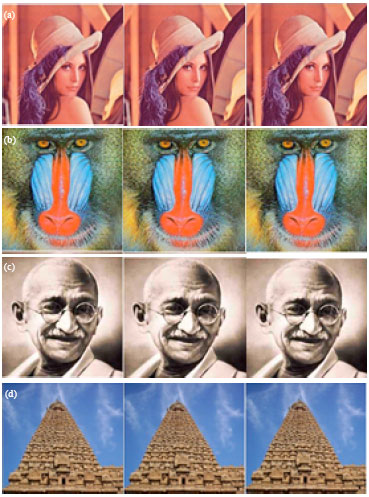
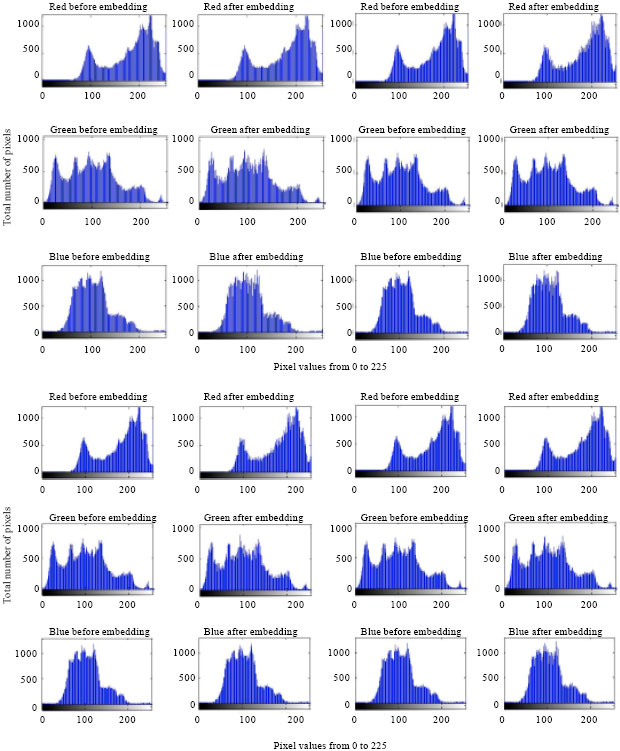
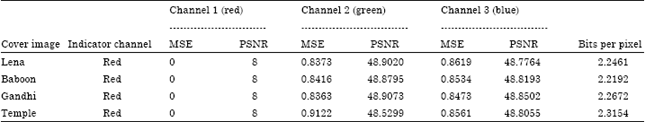
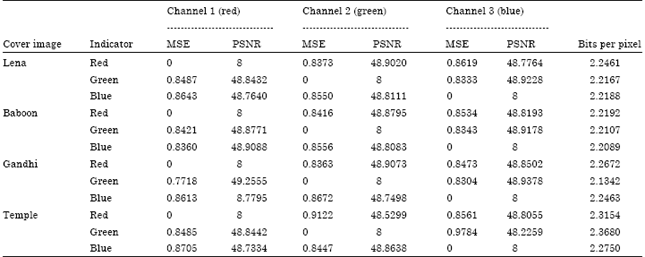
Aparna Reply
Hi All,
Hats off on your work. I am an avid kolam lover and regularly follow the practice of drawing kolams in our front yard. Being a communications engineer myself, I was amazed at the fact that Kolams could be a basis of secure patterns generation algorithm. The one person who to whom i could speak about this research would be my grandmother who is almost 90 and would certainly be happy to know that her practice of drawing kolams till date is not trivial and has contributed to incredible research studies like this.
Thank you so much and keep up your good work!
Cheers
Karthikeyan Krishnamourthy
Hi Aparna, Thanks for your kind words. This would surely encourage us all. The idea of using Kolam for information security was inspired by our work of our Mentors, Dr. Rengarajan and Dr. Rayappan.
Thanks again and we are happy that we could make your grandmother happy.
Regards,
Karthik
Dr Rengarajan Amirtharajan
Thanks a lot madam. Inspiration for this work is my mother.Hats off to her