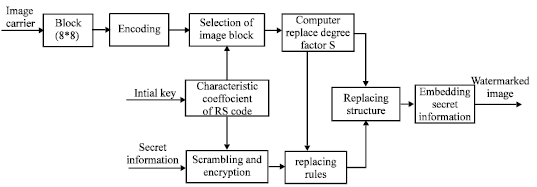
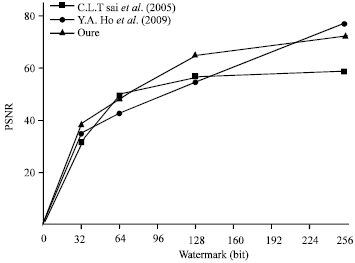
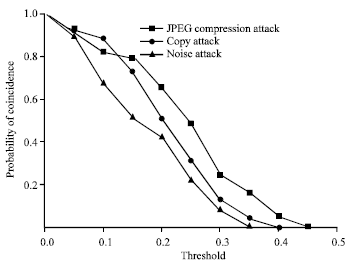
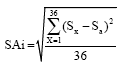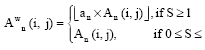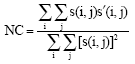Research Article
A High-capacity Lossless Algorithm for Watermarking Binary Images
School of Computer Science and Engineering, Hunan University of Science and Technology, Xiangtan, 411201, China
Jianbo Xu
School of Computer Science and Engineering, Hunan University of Science and Technology, Xiangtan, 411201, China
Jing Long
School of Computer Science and Engineering, Hunan University of Science and Technology, Xiangtan, 411201, China