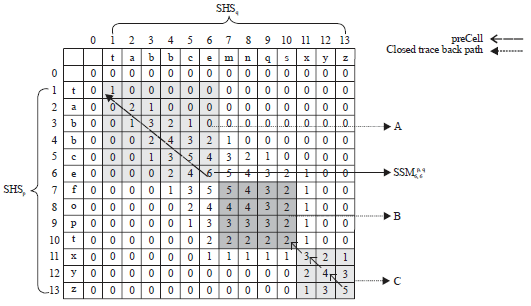
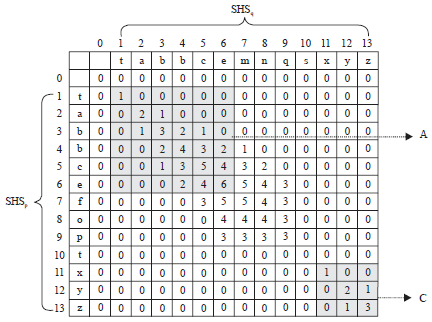
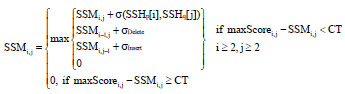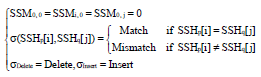Research Article
Detection of Code Clone Based on Source Fragment Alignment
School of Computer Science and Technology, Hangzhou Dianzi University, 310018 Hangzhou, China
Dongjin Yu
School of Computer Science and Technology, Hangzhou Dianzi University, 310018 Hangzhou, China
Xiang Shu
School of Computer Science and Technology, Hangzhou Dianzi University, 310018 Hangzhou, China