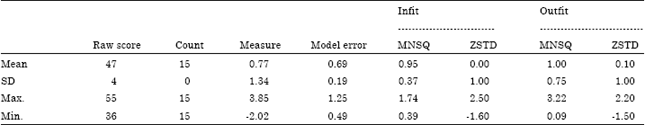
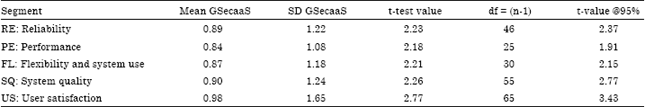
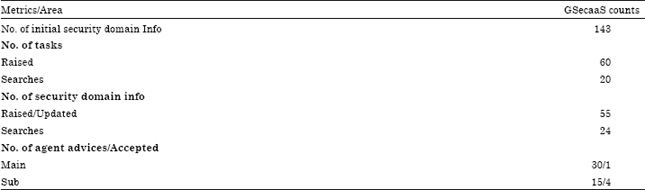
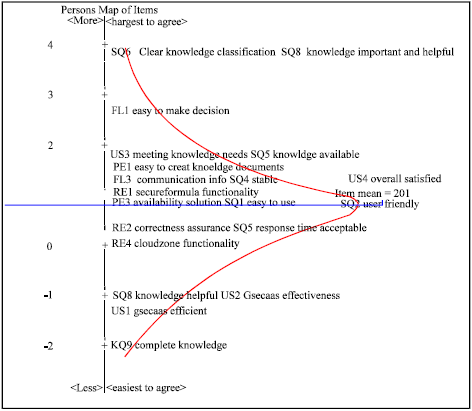
Research Article
Security Facilitation in Collaborative Cloud Data Storage Implementation Environment Based on Multi Agent System Architecture
Department of IT, Information System, Faculty of Computer Science and IT, University Putra Malaysia, 43400 UPM, Serdang, Selangor, Malaysia
Rodziah Atan
Department of IT, Information System, Faculty of Computer Science and IT, University Putra Malaysia, 43400 UPM, Serdang, Selangor, Malaysia
Rusli Abdullah
Department of IT, Information System, Faculty of Computer Science and IT, University Putra Malaysia, 43400 UPM, Serdang, Selangor, Malaysia
Masrah Azrifah Azmi Murad
Department of IT, Information System, Faculty of Computer Science and IT, University Putra Malaysia, 43400 UPM, Serdang, Selangor, Malaysia