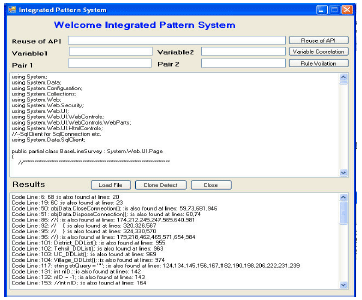
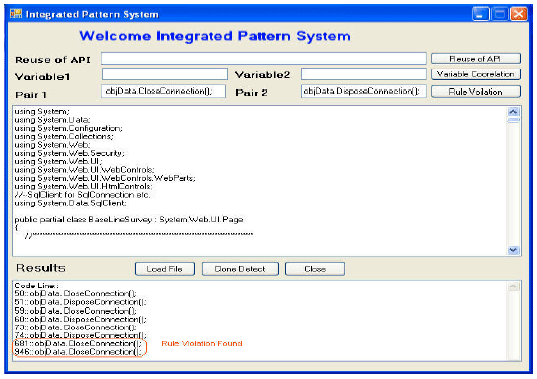
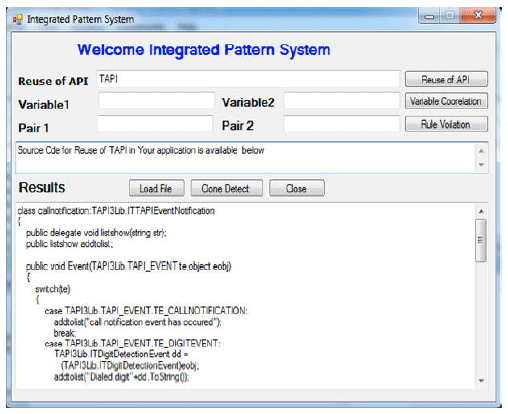
Research Article
A Framework for Automatically Mining Source Code
School of Computer and Applied Technology, Huazhong University of Science and Technology (HUST), Wuhan, China
Guohui Li
School of Computer and Applied Technology, Huazhong University of Science and Technology (HUST), Wuhan, China
Rana Muhammad Ashfaq
Department of Computer Science, International Islamic University, Islamabad, Pakistan