Research Article
Adaptive Data Hiding Based on Visual Cryptography
Saranathan College of Engineering, Trichirapalli, Tamil Nadu, India
Y. Venkataramani
Saranathan College of Engineering, Trichirapalli, Tamil Nadu, India
At the budding of security developments, cryptography was introduced which completely destroys the user perspective of viewing and transforms the content to something that is unrecognized data. This could sustain for basic security, but as the threats started rising, cryptography succumbed as the process is well known to the viewer. As an enhancement, method whose changes are unperceivable irrespective of any operation was required. This got steganography and watermarking to limelight (Stefan and Fabin, 2000). Cryptography is an art of providing data security using methods of encryption and decryption (Schneier, 2007).
Cryptography lends a helping hand in keeping information safe and sound (Schneier, 2007). This is its ultimate aim for which the modern era version has come up with vast and different practices and procedures for real time application. Scores of cryptic algorithms are formulated for security’s sake and of which the one that has recently found surprising is the expanse of Visual Cryptography (Noar and Shamir, 1995; Amirtharajanet al., 2013a, b) . It of course, has its origin from conventional cryptography. In simple words to put it, message to be communicated (secret) to the other end undergoes segmentation and is sent in operated forms. Thus, at the receiving end, one has to merge all the segments in a right way to read the secret.
Visual cryptography is a branch of cryptography concerned with providing data security using black and white pixels. As the name indicates, visual cryptography is based on human vision. It uses the characteristics of human vision to decipher the original message from the scrambled or encrypted images. It is an emerging trend of cryptography which uses the concept of shares. It assumes that the message consists of black and white pixels and each pixel appears in ‘n’ modified forms. These modified forms are called shares (Noar and Shamir, 1995; Amirtharajan et al., 2013a, b). Unlike other techniques, it does not require any knowledge of cryptography techniques. Also, it does not require any complex computations. Hence it is simple and self-sufficient in providing data security. Visual cryptography guarantees that hackers cannot comprehend the ideas about a secret image from different cover images. For instance, if there are ‘n’ images, then there shall be a constant ‘k’ of such images. Hence the secret can be revealed with ‘n’ or ‘n-1’ such images but not just with ‘k’ images. This comes from the fact that the output media of visual cryptography are transparencies as shown in Fig. 1. This term evolves from the way the white pixels of black and white images are considered as transparent. This method, also known as the black and white visual cryptography breaks down every pixel of the secret image into a 2x2 block. Hence the cover can be shared among a group of ‘n’ people.
Steganography invented by the Greek is a method of “covered writing” where only the beneficiary knows the existence of the secret message apart from the sender, even if were available on a public forum (Amirtharajan et al., 2011, 2012, 2013c-i; Amirtharajan and Rayappan, 2012a-d; Cheddad et al., 2010; Hmood et al., 2010a, b; Janakiraman et al., 2012a, b; Padmaa et al., 2011; Thenmozhi et al., 2012).
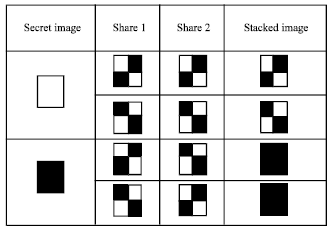 | |
| Fig. 1: | Visual cryptography shares |
The secret message is transformed into a stego message when it is embedded on an innocent carrier medium i.e., a document (Al-Azawi and Fadhil, 2010; Xiang et al., 2011; Yang et al., 2011), picture, Image (Al-Frajat et al., 2010; Amirtharajan et al., 2011, 2012, 2013c-i; Amirtharajan and Rayappan, 2012a-d, 2013; Chan and Cheng, 2004; Hmood et al., 2010a, b; Janakiraman et al., 2012a, b; Zanganeh and Ibrahim, 2011) or an audio file (Zhu et al., 2011).
The image post the embedment of the data is known as stego image is then sent into a public forum which can be accessed by the intended user or even the general public (Chang et al., 2003; Chang and Tseng, 2004; Hong et al., 2009; Zhao and Luo, 2012). The only difference would be that the public would not even suspect the presence of any hidden messages (Luo et al., 2008, 2011; Praveenkumar et al., 2012a, b, 2013a, b; Mohammad et al., 2011; Xiang et al., 2011; Yang et al., 2011); however, the user would have known the presence of a message and will also know how to extract it. Steganography alone is not robust technique as a statistical analysis would give away the presence of a secret message (Stefan and Fabin, 2000). Steganography needs to be coupled with techniques to fortify the algorithm and protect the data (Mohammad et al., 2011; Rajagopalan et al., 2012; Zaidan et al., 2010).
This study proposed a method to combine Visual Cryptography (VC) with random image steganography (RIS). The next section describes the proposed method with neat diagram and algorithm, to combine VC with RIS in material and methods followed by the result and discussion with comparative existing methods. The final section explorers the conclusion of this study.
Cryptography enables information security by employing techniques in which the data is scrambled by a key in the process called encryption and re scrambling the encrypted message again with the key in order to get back the original data in the process called decryption. Here, the key plays a vital role. Without the correct key, the scrambled message cannot be recovered (Hou, 2003). Visual cryptography assumes that the message consists of black and white pixels and each original pixel appears in n modified versions called shares (Amirtharajan et al., 2013a-b). Each share is a collection of m black and white sub pixels and is generated by doing mathematical operation between subset (n X m) of original message and permuted version of any one of the two (n X m) random matrix Noar and Shamir (1995).
In Steganography the confidential information is embedded into innocent looking cover objects, such as digital images (Chang et al., 2003; Chang and Tseng, 2004; Chan and Cheng, 2004; Cheddad et al., 2010; Thanikaiselvan et al., 2012a-b, 2013). In this proposed method, visual cryptography and tri color random image steganography is combined for multiple users. Figure 2 represents the basic block diagram for this proposed method. For embedding, input color image can be taken as secret. To make encryption easy, color image should be converted into gray scale image. Dithering is used to convert gray image into binary image. By using (k, n) threshold scheme, shares are generated (Noar and Shamir, 1995) and these shares are once again encrypted with different keys. Then these encrypted shares are embedded in the cover image using Pixel indicator method.
In pixel indicator method (Gutub, 2010; Padmaa et al., 2011; Padmaa and Venkataramani, 2010) any one of the color plane is treated as indicator plane and remaining two planes are used to embed the data. The color plane for data embedding is decided by the last two bits of the pixel of indicator plane. The number of bits to be embedded is decided by calculating the difference value d between the maximum pixel value and the minimum pixel value of three neighbor pixels (Padmaa et al., 2011) and the quality of stego image is enhanced by OPAP method (Chan and Cheng, 2004). There are more explanation on steganography methods and its advantages are available in Amirtharajan et al. (2011, 2012, 2013c-i) and Zanganeh and Ibrahim (2011). For recovery, stego image is considered. Based on the last two LSB bits of each pixel in the indicator plane, the shares are recovered by using PVD method and then descrambled by using the keys (Gutub, 2010).
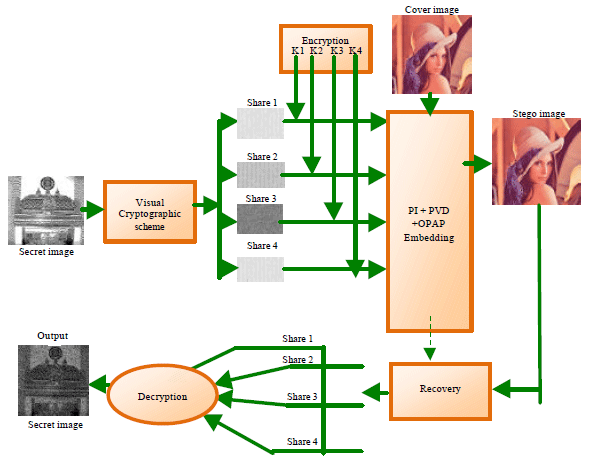 | |
| Fig. 2: | Block diagram of proposed method |
These descrambled shares are stacked and extracted and then split into shares by decryption with keys which have been used in encryption. Then these decrypted shares are stacked and the original secret image is obtained.
EMBEDDING ALGORITHM
| Method 1: | |
 | |
RECOVERY ALGORITHM
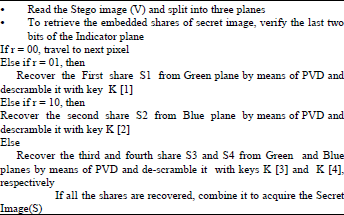 |
| Method 2: | Embedding algorithm |
  | |
| Recovery algorithm: | |
 | |
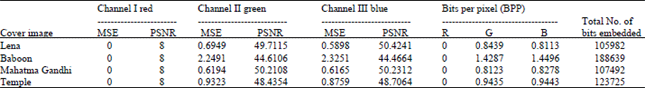
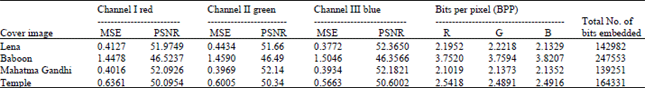
In this execution, four cover color images Lena, Baboon, Mahatma Gandhi and Temple of size 256x256 are chosen for embedding. The cover and stego images along with their histograms are shown in Fig. 3-10. This algorithm is simulated in MATLAB 7.1. To have an idea about effectiveness of the system, MSE, PSNR, BPP and embedding capacity are calculated and tabulated in Table 1, 2 and 3. The equations are:
![]()
![]()
Embedding Capacity = Bits per pixel×No. of pixels in the cover image
For the chosen images, full embedding capacity for the two methods is examined here. Method 1 takes RED as indicator; as per the algorithm no embedding is done in this plane. It is clear from the table that all the images exhibit high PSNR.
| Table 1: | MSE, PSNR values for method 1 |
 | |
| Table 2: | MSE, PSNR values for method 2 |
 | |
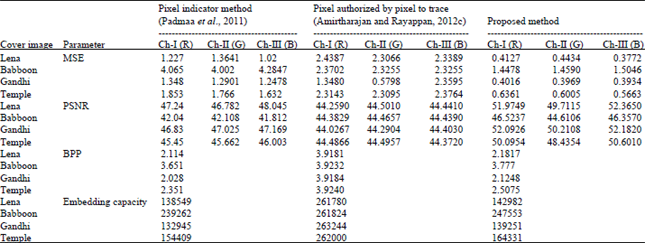
| Table 3: | Comparative estimation parameters of the proposed embedding method 2 |
 | |
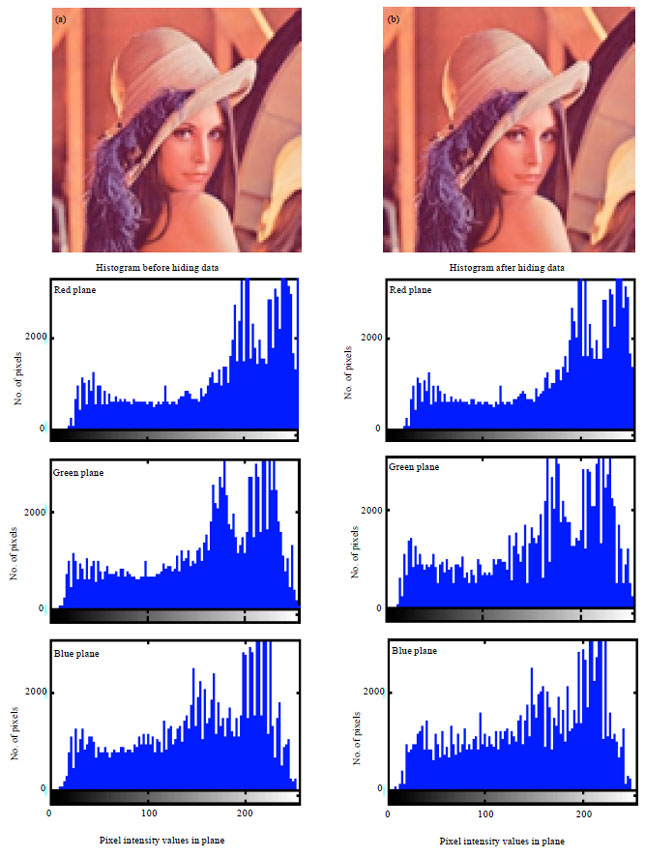 | |
| Fig. 3(a-b): | (a) Cover and (b) Stego images of Lena and their corresponding histograms |
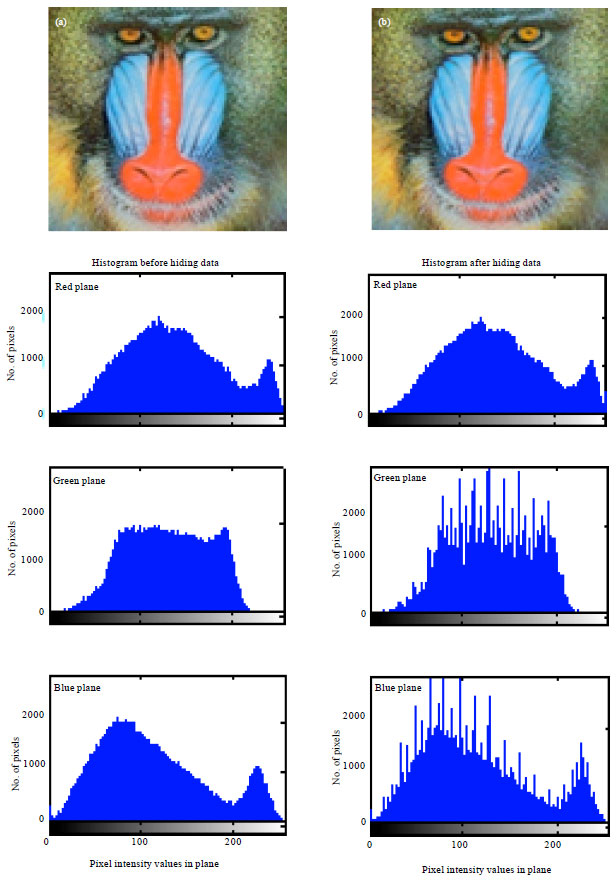 | |
| Fig. 4(a-b): | (a) Cover and (b) Stego images of Baboon and their corresponding histograms |
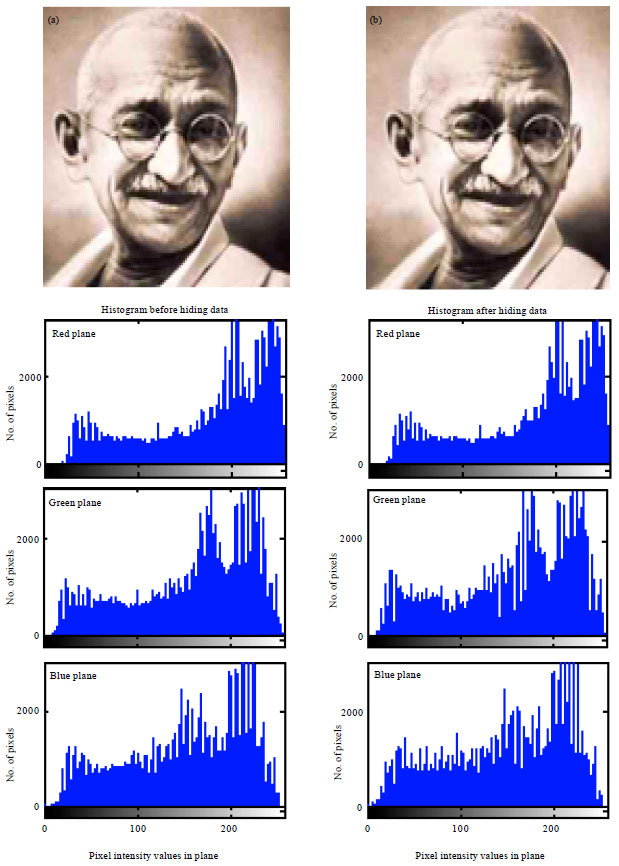 | |
| Fig. 5(a-b): | (a) Cover and (b) Stego images of Mahatma Gandi and their corresponding histograms |
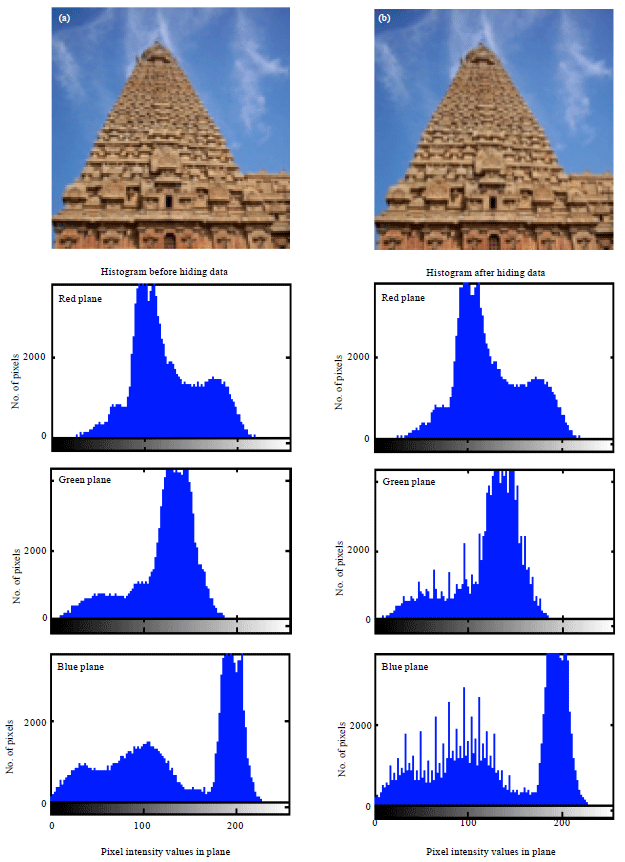 | |
| Fig. 6(a-b): | (a) Cover and (b) Stego images of Temple and their corresponding histograms |
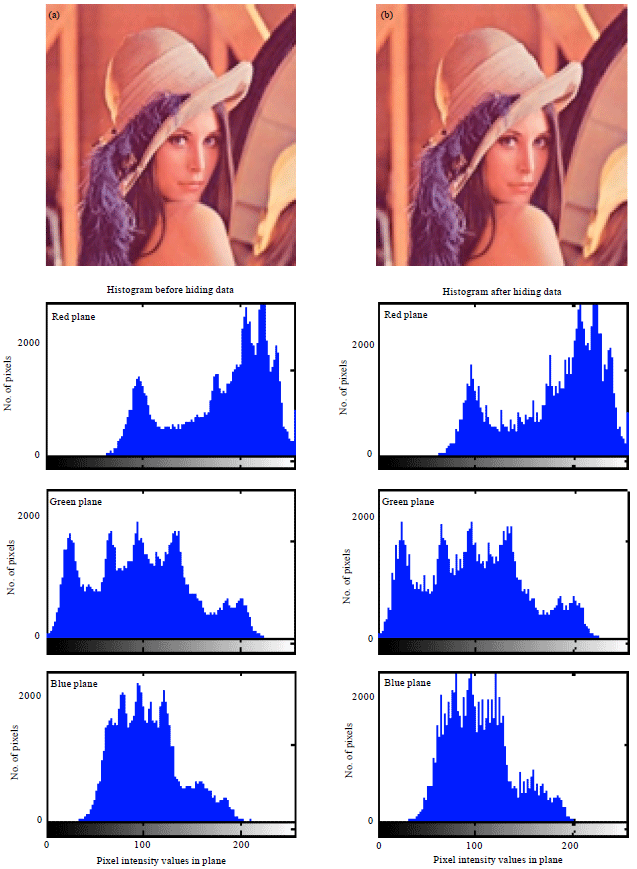 | |
| Fig. 7(a-b): | (a) Cover and (b) Stego images of Lena and their corresponding histograms |
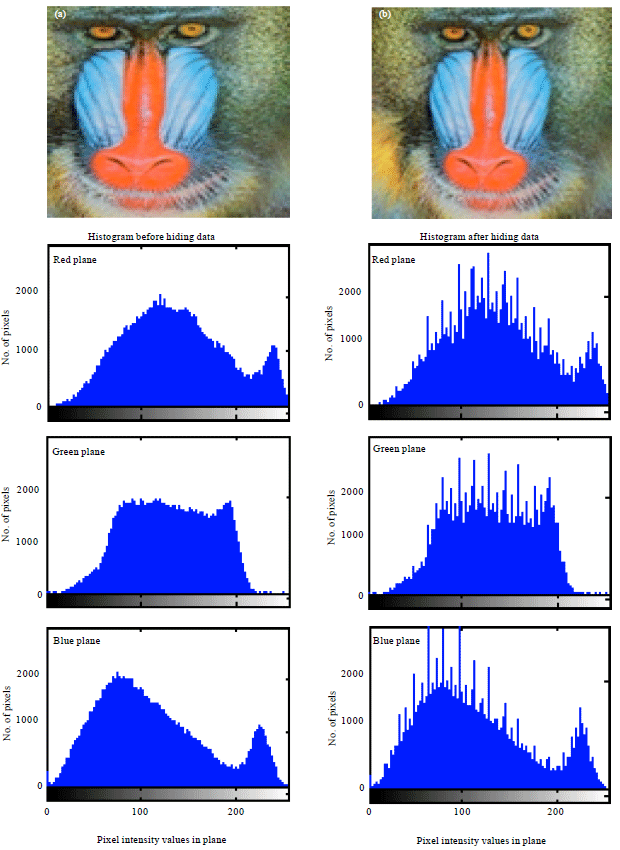 | |
| Fig. 8(a-b): | (a) Cover and (b) Stego images of Baboon and their corresponding histograms |
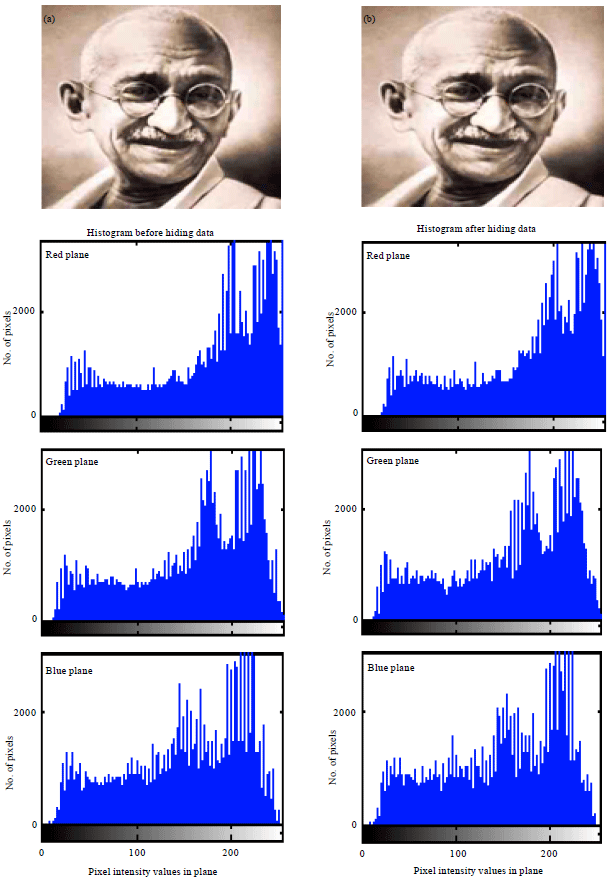 | |
| Fig. 9(a-b): | (a) Cover and (b) Stego images of Mahatma Gandhi and their corresponding histograms |
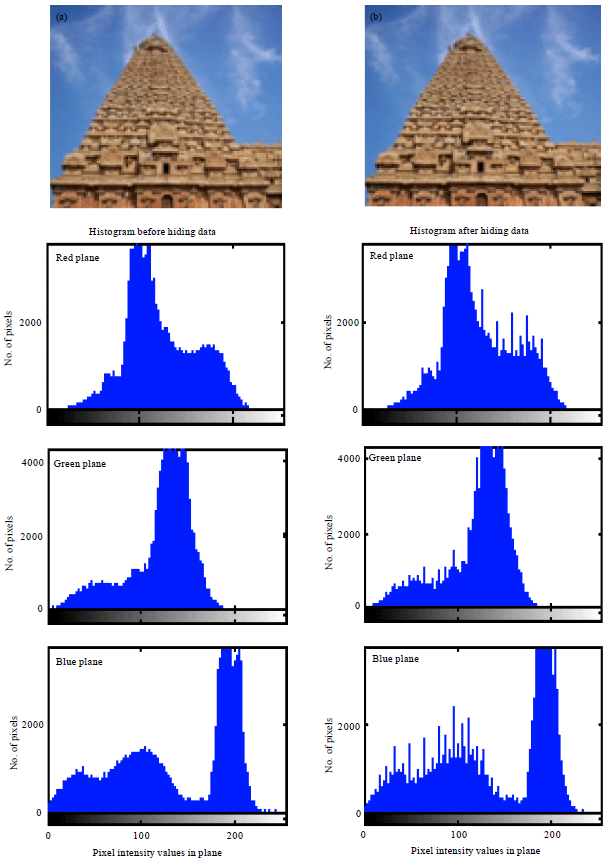 | |
| Fig. 10(a-b): | (a) Cover and (b) Stego images of Temple and their corresponding histograms |
In general, PSNR of above 38 dB is rendered good. So, all these images possess high PSNR, which indicates high imperceptibility; that is the images are prone to visual attack and escape it. Thus one cannot sense the hidden data in the images. Conversely, MSE is very low. But Baboon has relatively high MSE of all. In turn it has the highest embedding capacity. Relatively decent BPP is obtained in all images. Also, high embedding capacity highlights this routine. Indicator is cyclically selected in method 2, where each plane will have a chance of being the indicator. The images possess high BPP and also embedding capacity is also high. Approximately, 2.6445 bits are embedded in each plane which is determined to be fair. Thus, method 2 gives anticipated results and is best. This method exhibit higher imperceptibility, security and is highly robust to steganalytic attacks.
Comparison of existing methods with proposed method: In pixel indicator method (Padmaa et al., 2011), any one of the colour planes is assumed to be the indicator and data is embedded accordingly. In pixel authorised by pixel with pixel indicator method (Amirtharajan and Rayappan, 2012c), Hilbert SFC and Moore SFC traversing path based steganography techniques are applied. Here a block of 4x4 pixels are taken and the above methods are implemented on it by adapting a common traversing path for the sender and receiver. Then the entire cover image is taken for secret bit embedding by considering it as multiple 4x4 blocks to cover up the entire 28x28x3 pixels. The pixel indicator method here is used to select a particular channel as an indicator. Then data embedding in other channels is done based upon the last two bits of the indicator.
In this proposed method, Cryptography, Visual Cryptography and Steganography are put together to enhance the security and robustness. The method minimizes the perceptibility of the introduced distortion. Compared with Pixel indicator and Pixel authorized by pixel to trace with Pixel indicator methods, our proposed method makes stego-image so strong. Four parameters namely MSE, PSNR, BPP and embedding capacity are used as metrics for comparison. Visual cryptography with steganography will provide minimum MSE and maximum PSNR and moderate embedding capacity. These parameters decide the imperceptibility and robustness of a stego-image. This method provides better resistance against various forms of attacks.
The first author expresses her sincere gratitude to Dr. R. Amirtharajan Associate Professor/ECE School of Electrical and Electronics Engineering, for his guidance in providing technical and linguistic support for fructifying the quality of this study.