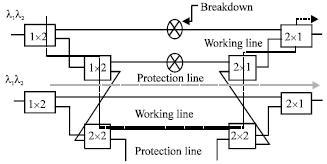
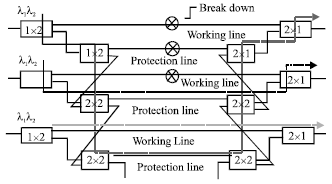
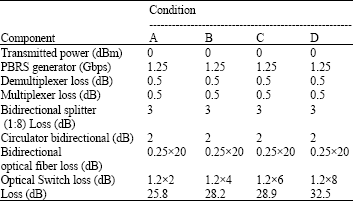
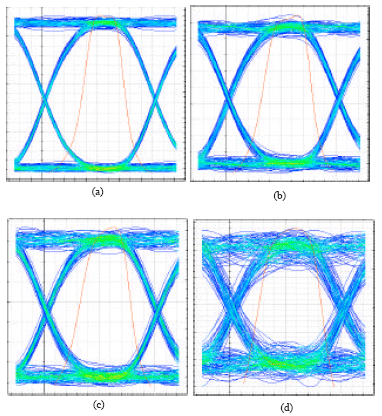
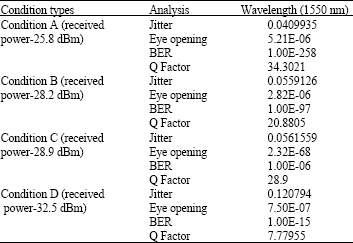
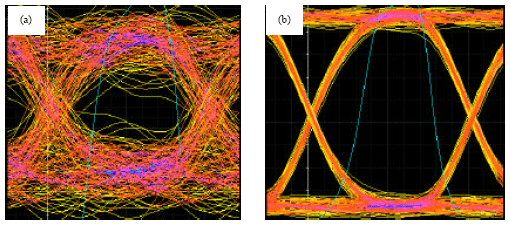
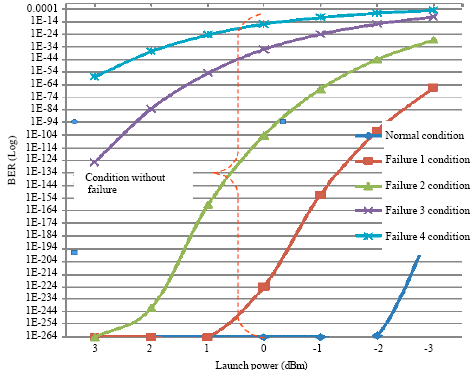
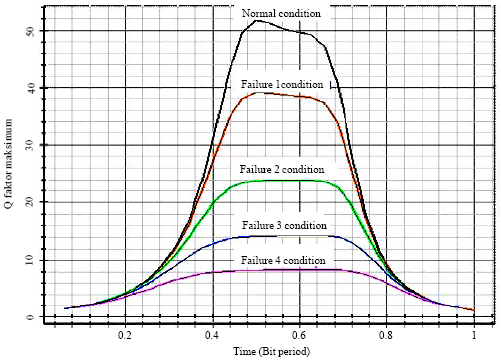
Research Article
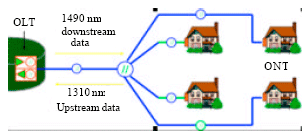
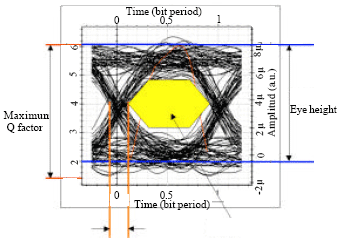
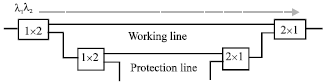
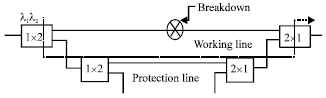
The Eye Diagram Analysis of Restoration Scheme in FTTH-PON
Spectrum Technology Research Division, Computer and Network Security Research Group, Department of Electrical, Electronic and Systems Engineering, Faculty of Engineering and Built Environment, Universiti Kebangsaan Malaysia, 43600 UKM Bangi, Selangor, Malaysia
L. Al-Hakim Azizan
Spectrum Technology Research Division, Computer and Network Security Research Group, Department of Electrical, Electronic and Systems Engineering, Faculty of Engineering and Built Environment, Universiti Kebangsaan Malaysia, 43600 UKM Bangi, Selangor, Malaysia
S. A. C. Aziz
Spectrum Technology Research Division, Computer and Network Security Research Group, Department of Electrical, Electronic and Systems Engineering, Faculty of Engineering and Built Environment, Universiti Kebangsaan Malaysia, 43600 UKM Bangi, Selangor, Malaysia
K. Jumari
Spectrum Technology Research Division, Computer and Network Security Research Group, Department of Electrical, Electronic and Systems Engineering, Faculty of Engineering and Built Environment, Universiti Kebangsaan Malaysia, 43600 UKM Bangi, Selangor, Malaysia