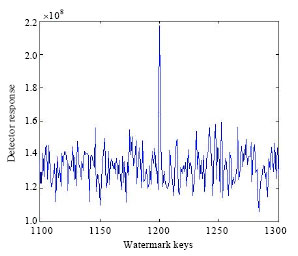
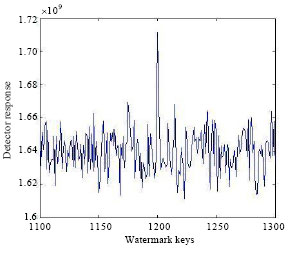
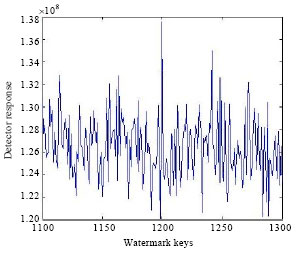
Research Article
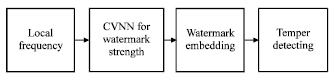
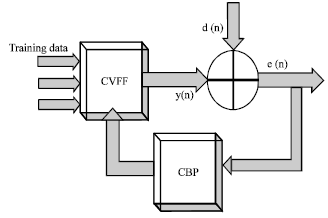
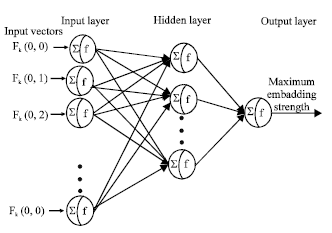
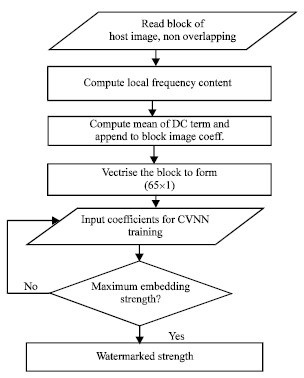
Determining Watermark Embedding Strength using Complex Valued Neural Network
International Islamic University Malaysia (IIUM), P.O. Box 10, 50728, Kuala Lumpur, Malaysia
O. O. Khalifa
International Islamic University Malaysia (IIUM), P.O. Box 10, 50728, Kuala Lumpur, Malaysia
Aisha Abdulla
International Islamic University Malaysia (IIUM), P.O. Box 10, 50728, Kuala Lumpur, Malaysia
A. A. Aburas
International Islamic University Malaysia (IIUM), P.O. Box 10, 50728, Kuala Lumpur, Malaysia
A. M. Zeki
International Islamic University Malaysia (IIUM), P.O. Box 10, 50728, Kuala Lumpur, Malaysia