Research Article
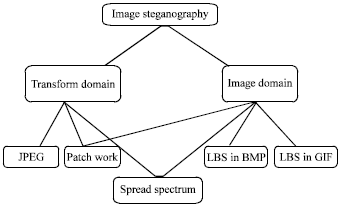
An Overview on Hiding Information Technique in Images
Faculty of Computer Science and Information Technology, University Malaya, 50603 Kuala Lumpur, Malaysia
B.B. Zaidan
Faculty of Engineering, Multimedia University, Jalan Multimedia, 63100 Cyberjaya, Malaysia
A.A. Zaidan
Faculty of Engineering, Multimedia University, Jalan Multimedia, 63100 Cyberjaya, Malaysia
Hamid A. Jalab
Faculty of Computer Science and Information Technology, University Malaya, 50603 Kuala Lumpur, Malaysia