Research Article
Fast Detection Anti-Collision Algorithm for RFID System Implemented On-Chip
Department of Electrical and Electronics System, Faculty of Engmeenng, National University of Malaysia, 43600, Malaysia
Masuri Othman
Institute of Microengineermg and Nanoelectronic (IMEN), National University of Malaysia, 43600, Malaysia









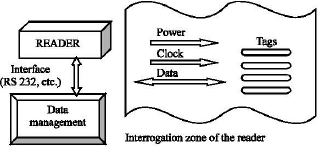
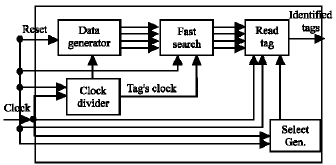
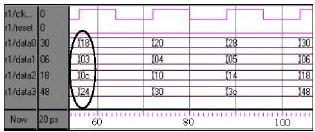
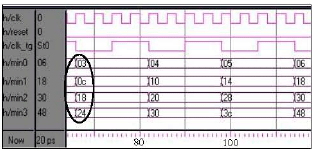
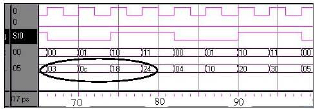

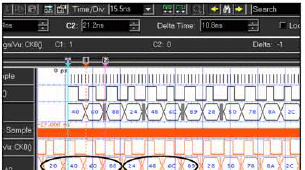
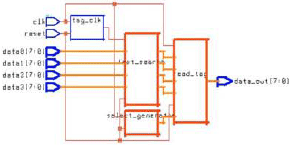

ARJUNA MARZUKI Reply
I cannot see the 'on chip' work. Maybe the authors could relate the info to me?