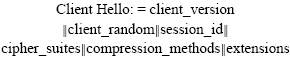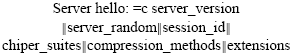Research Article
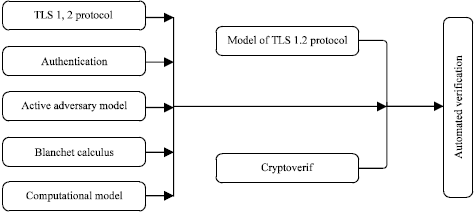
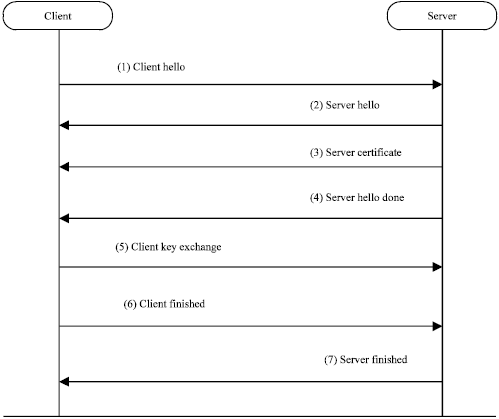
Mechanized Verification of Security Properties of Transport Layer Security 1.2 Protocol with Crypto Verif in Computational Model
School of Computer, South-Center University for Nationalities, MinYuan Road # 708, HongShan Section, 430074, Wuhan, Hubei, China
Leyuan Niu
School of Computer, South-Center University for Nationalities, MinYuan Road # 708, HongShan Section, 430074, Wuhan, Hubei, China
Yitong Yang
School of Computer, South-Center University for Nationalities, MinYuan Road # 708, HongShan Section, 430074, Wuhan, Hubei, China
Zimao Li
School of Computer, South-Center University for Nationalities, MinYuan Road # 708, HongShan Section, 430074, Wuhan, Hubei, China