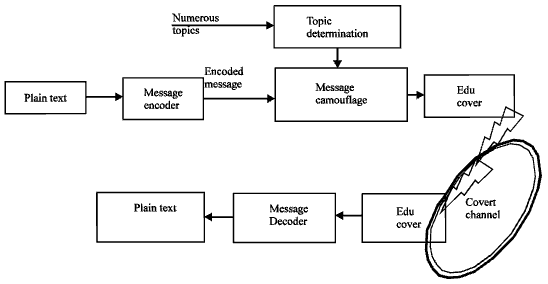
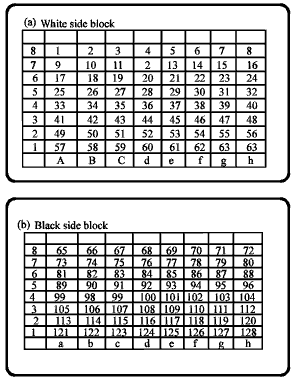
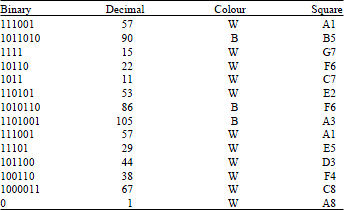
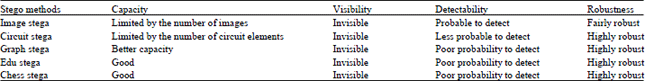
Research Article
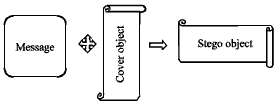
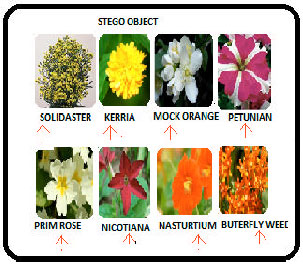
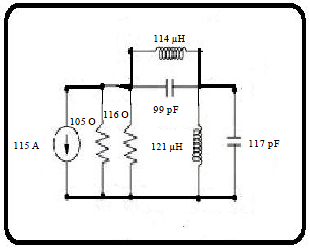
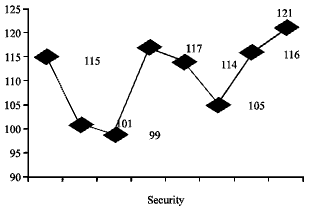
Cover G for 3 and 4 G-A Stego Product
Department of ECE, School of Electrical and Electronics Engineering SASTRA University, India
Imaculate Rosaline
Department of ECE, Oxford Engineering College, Tamil Nadu, India
Rengaraja Swamy
Department of ECE, Oxford Engineering College, Tamil Nadu, India
Sai Pavan
Department of ECE, School of Electrical and Electronics Engineering SASTRA University, India
R. Sridevi
Department of Physics, A.V.V.M Sri Pushpam College, Poondi, Thanjavur, 613-503, India
J.B.B. Rayappan
Department of ECE, School of Electrical and Electronics Engineering SASTRA University, India