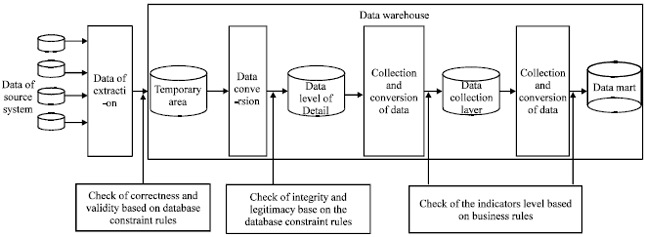
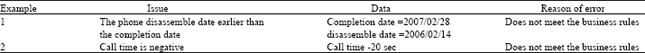
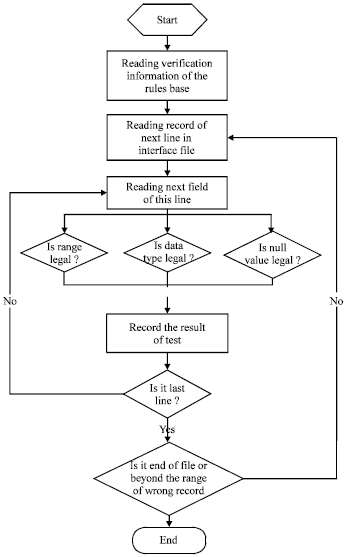
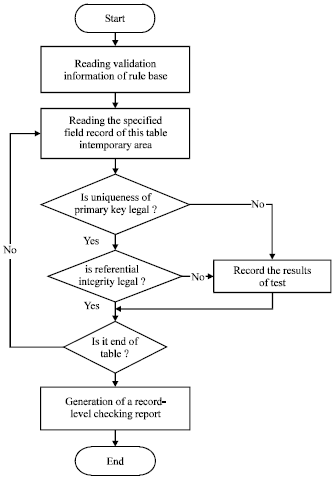
Research Article
Research of Data Quality Assurance about ETL of Telecom Data Warehouse
Department of Information Engineering, Shaanxi Polytechnic Institute, Shaanxi, Xian�yang, 712000, China
Wei Wei
School of Computer Science and Engineering, XI ` an University of technology, XI�an 710048, China
Jing Zhang
School of Computer Science and Engineering, XI ` an University of technology, XI�an 710048, China
Wei Wang
School of Computer Science and Engineering, XI ` an University of technology, XI�an 710048, China
Jinwei Zhao
School of Computer Science and Engineering, XI ` an University of technology, XI�an 710048, China
Junhuai Li
School of Computer Science and Engineering, XI ` an University of technology, XI�an 710048, China
Peiyi Shen
National School of Software, Xidian University, 710071, Xi`an, Shaanxi, Peoples Republic of China
Xiaoyan Yin
Department of Computer Science and Technology, Northwest University, Xi`an 710127, China
Xiangrong Xiao
School of Information Engineering, Zhejiang Agriculture and Forest University, China
Jie Hu
School of Computer Science and Engineering, XI ` an University of technology, XI�an 710048, China