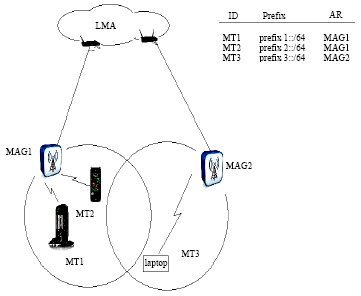
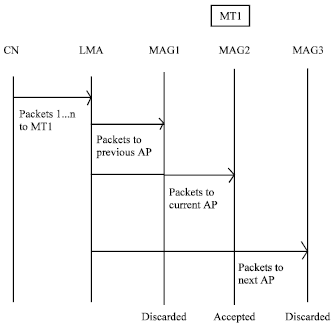
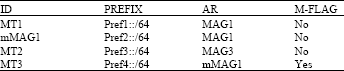
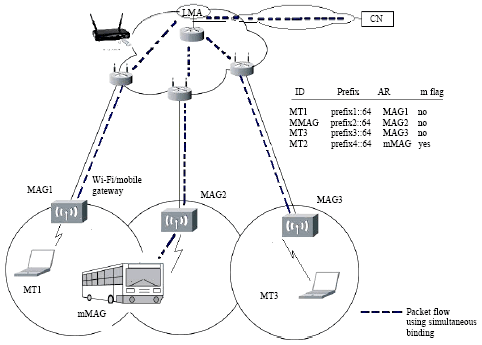
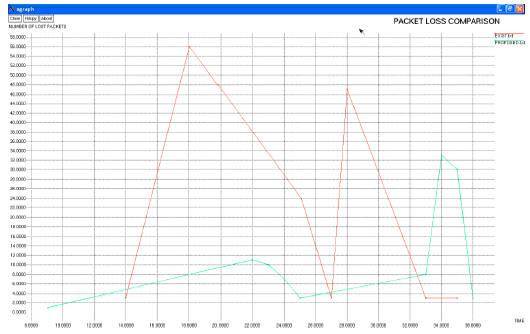
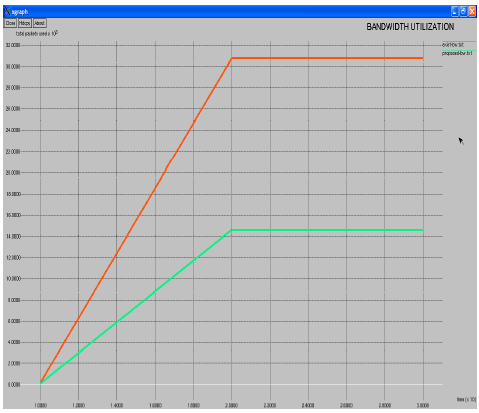
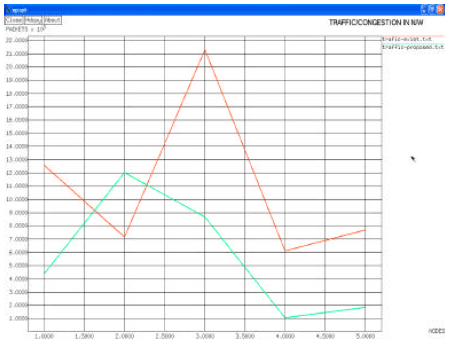
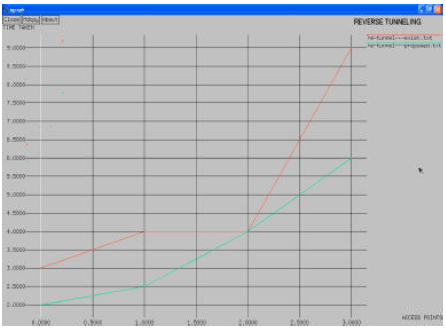
Research Article
Improving the Performance of Packet Transfer in Network Mobility
School of Information Technology and Engineering, VIT University, South India
P. Balasubramanie
Department of Computer Technology, Kongu Engineering College, South India