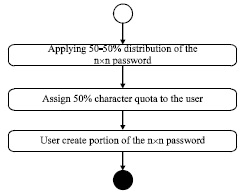
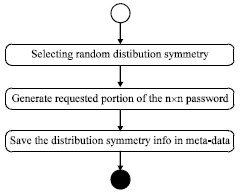
Research Article
Effective Methods for Secure Authentication in Vulnerable Workflows using nxn Passwords
Department of Computer and Information Sciences, Universiti Teknologi PETRONAS, Malaysia
M.F. Hassan
Department of Computer and Information Sciences, Universiti Teknologi PETRONAS, Malaysia
M.A. Qureshi
Department of Computer and Information Sciences, Universiti Teknologi PETRONAS, Malaysia
R. Akbar
Department of Computer and Information Sciences, Universiti Teknologi PETRONAS, Malaysia