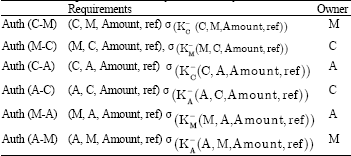
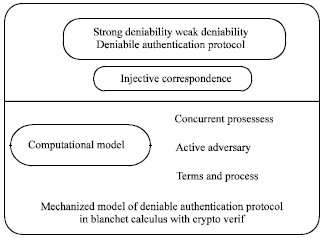
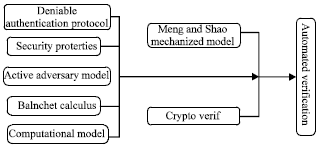
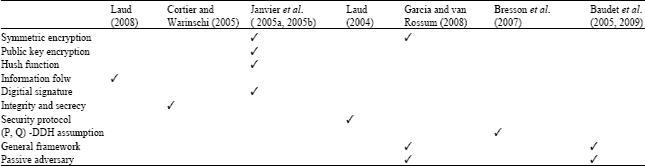
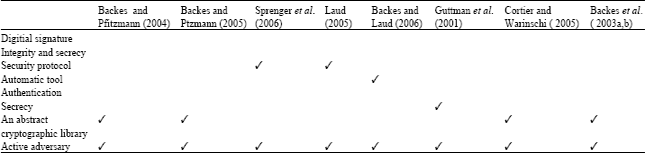
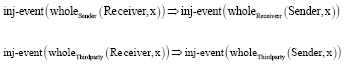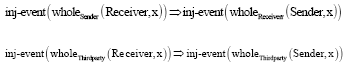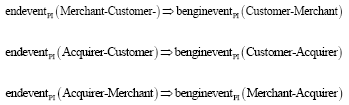Review Article
A Survey on Analysis of Selected Cryptographic Primitives and Security Protocols in Symbolic Model and Computational Model
School of Computer, South-Center University for Nationalities, MinYuan Road No. 708, HongShan Section, Wuhan, Hubei, China, 430074