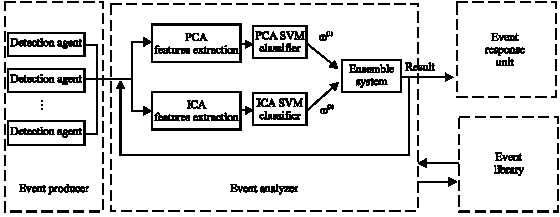
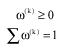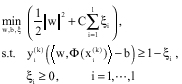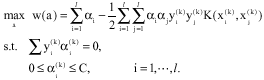Research Article
PCA-ICA Ensembled Intrusion Detection System by Pareto-Optimal Optimization
School of Electronic and Information Engineering, Xi`an Jiaotong University, Xi`an 710049, China
Bo Zhou
Yunnan Institute of Technology and Information, Kunming 650000, China
Jiashu Zhao
School of Science, Xi`an Jiaotong University, Xi`an 710049, China