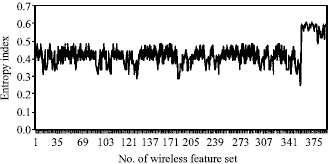
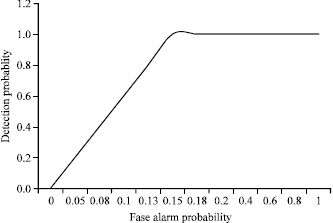
Research Article
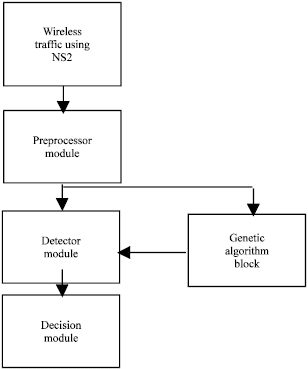
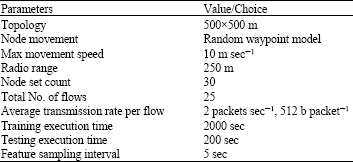
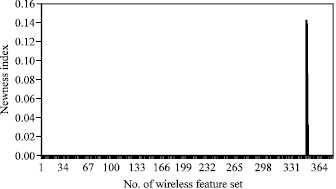
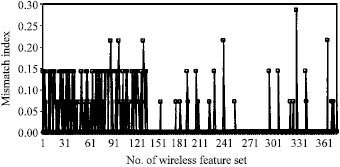
Wireless Node Misbehavior Detection Using Genetic Algorithm
Department of Electronics and Communication Engineering,Sri Venkateswara College of Engineering, Pennalur, Sriperumbudur, Tamilnadu 602105, India
M. Suganthi
Department of Electronics and Communication Engineering,Thiagarajar College of Engineering, Madurai 625015, India
R. Sunder
Department of Electronics and Communication Engineering,Sri Venkateswara College of Engineering, Pennalur, Sriperumbudur, Tamilnadu 602105, India