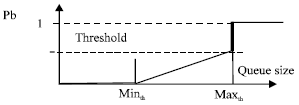
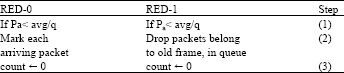
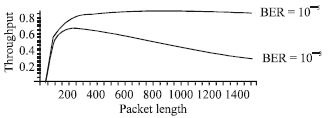
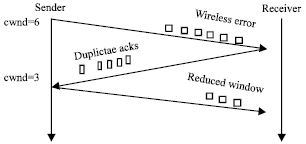
Research Article
TCP Protocol and Red Gateway Supporting the QoS of Multimedia Transmission Over Wireless Networks
Department of Design and Communication Systems, Anglia Ruskin University, United Kingdom
Sufian Yousef
Department of Design and Communication Systems, Anglia Ruskin University, United Kingdom
Jaafer AL- Saraireh
Department of Design and Communication Systems, Anglia Ruskin University, United Kingdom