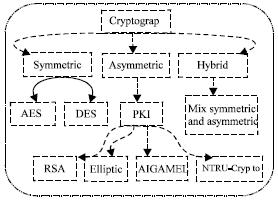
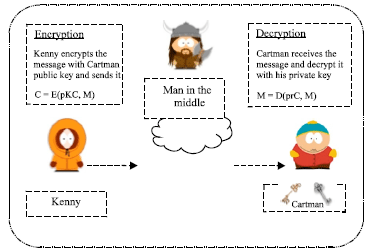
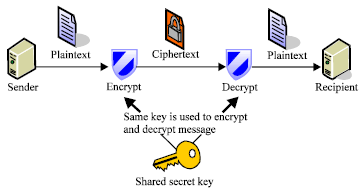
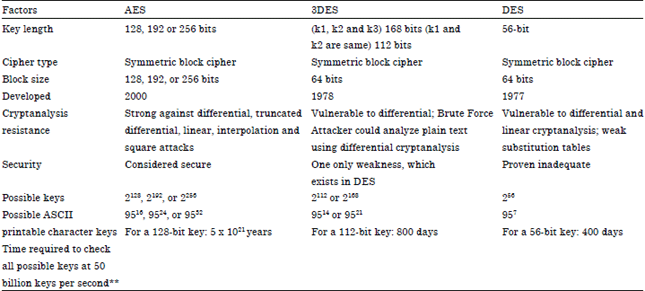
Review Article
Securing m-Government Transmission Based on Symmetric and Asymmetric Algorithms: A Review
Department of Systems and Networking, College of Information Technology, University Tenaga Nasional (UNITEN), Selangor, Malaysia
A.A. Zaidan
Network and Communication Security Research Group, ICT and Computational Science Research Cluster, University of Malaya, 50603 Kuala Lumpur, Malaysia
B.B. Zaidan
Network and Communication Security Research Group, ICT and Computational Science Research Cluster, University of Malaya, 50603 Kuala Lumpur, Malaysia